Proofpoint ITM has many special features that make it the ultimate enterprise-class user activity recording and auditing technology solution. But here are the top 5 that make us stand out as unique and powerful.
1) The first and most unique feature of Proofpoint ITM is that it captures ALL user activity taking place in a visual recording, while the system transcribes each user action into an easy-to-read summary (so that you don’t need to watch hours of video to know what took place). The content analysis data is immediately available forfree-text keyword searching. Search for names of applications run, windows opened, URLs accessed, keystrokes typed and much more. Every resulting search hit is linked directly to the portion of the video where that action occurred! This makes it incredibly easy to find the exact moment that an action was performed from among thousands of hours of video. Within each session, you can watch the full video replay of the user session and see exactly what took place. You can also navigate quickly through any session, using fast-forward/rewind or by jumping between each user command (similar to DVD chapter), start a replay mid-session at the exact time or action that you need. No more sitting through hours of unmarked video. The system records server and desktop sessionson Unix, Linux and Windows computers, accessed locally or remotely (Citrix, SSH, Telnet, Terminal Services, Remote Desktop, PC-Anywhere, VMware, etc.). In the images below you see two examples of the ITM console and it’s exact video playback taken from the audit list of videos and keyword-searchable activity logs of all user sessions on UNIX, LINUX, and Windows computers:
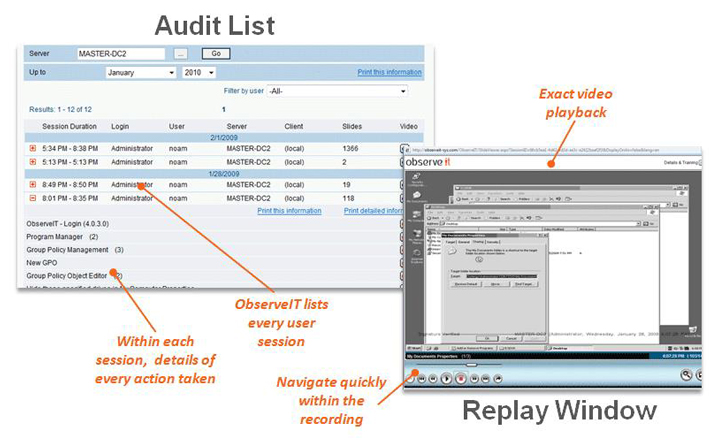
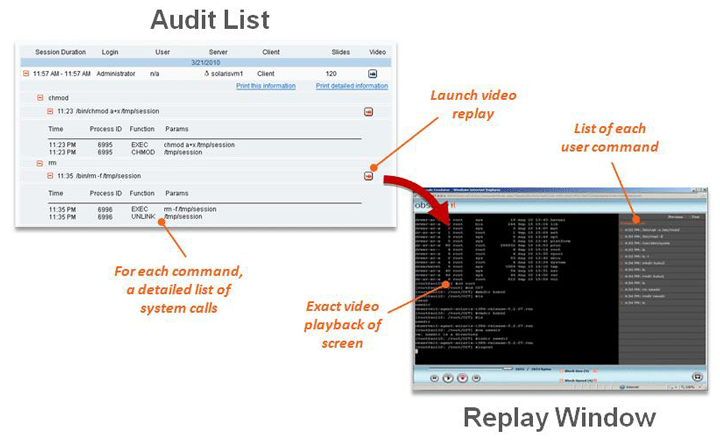
2) Generating human-readable logs for every app—even those that have no internal logs! Proofpoint ITM not only generates logs of every app, it even generates logs for apps that have no internal logs, and does all of this in clear and easy to understand “who did what” English. In other words, ITM generates logs based on actual user actions, transforming obscure system logs into a simple, human-readable format.
.jpg)
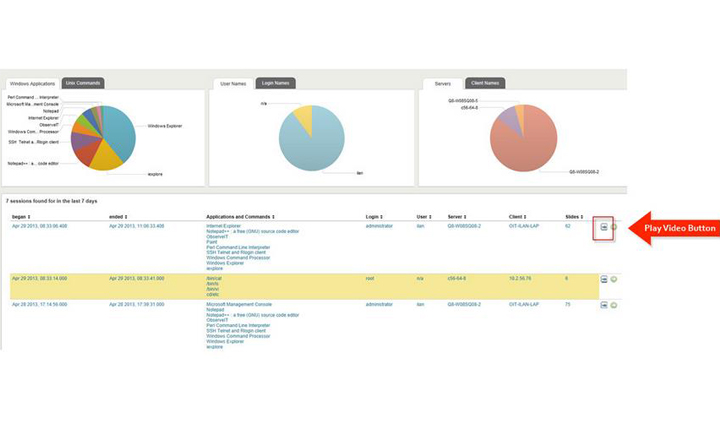
3) SIEM Integration–Proofpoint seamlessly integrates with third-party enterprise applications (such as log analysis, SIEM, IT ticketing, NMS and access control systems), boosting data security and regulatory compliance. Now you can boost your SIEM’s power to add user session data to SIEM dashboards and reports, correlate system log data with user activity data, fill in SIEM logging gaps, and improve regulation compliance and reduce security auditing costs by instantly finding user action and playing back relevant portions of recorded session videos. (In the photo above is an example of Proofpoint integrated with Splunk.) Below is an example of Proofpoint ITM integrating with Splunk’s SIEM, where you can now get a list of EVERY app run, detailed action list in simple to understand English, accompanied by a video clip showing the action taking place:
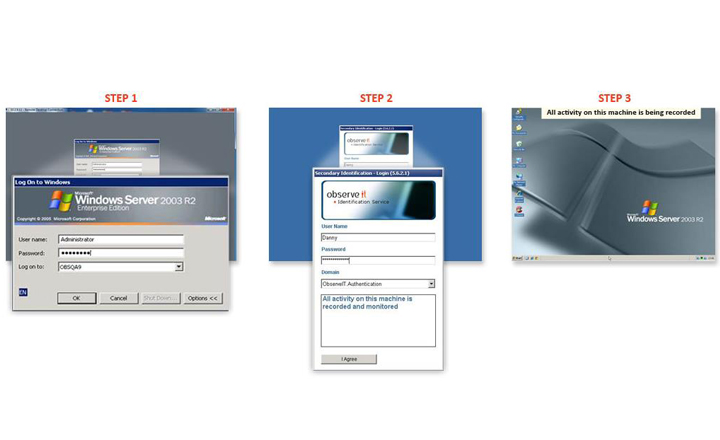
4) Secondary Identification–Proofpoint features a built-in privileged user identification solution which ensures unambiguous identification of individual users accessing shared accounts. After logging in to a Windows server using a shared account (in the standard login window), Proofpoint ITM requires valid individual credentials as well. This is an easy and cheap alternative to the only other common solution (expensive and complex password vaults).
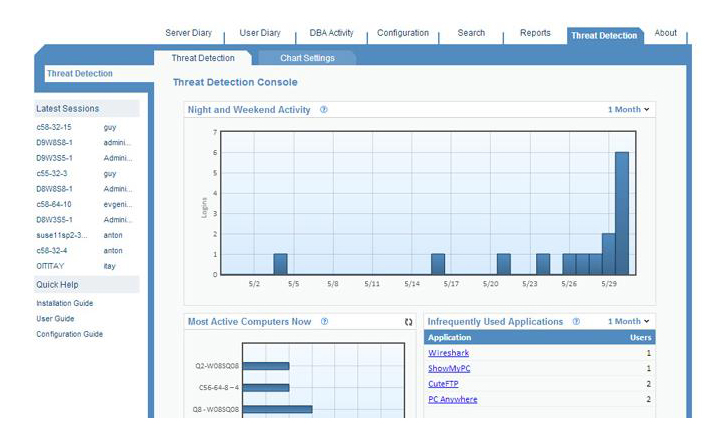
5) Threat Detection Console–The Proofpoint Threat Detection Console highlights suspicious activity on monitored computers, whether by outsiders or trusted users. This console contains seven charts as an important additional tool for IT administration and security staff to achieve early detection of data breaches and other attacks: (1) stay connected with the “Night and Weekend Activity” chart, tracking the number of logins which occurred outside regular working hours (days/hours are user-configurable), (2) follow the “Most Active Computers” to highlight unexpected over-usage of a server, which might indicate an attack, (3) keep a closer eye on “Infrequently Used Applications” to help identify the use of malicious ones that tend not to be commonly active, just as you would for (4) “Infrequently Used Computers“–a chart used for the least number of sessions, which can help identify suspicious use of a computer, as well as, (5) “Infrequently Used Login IDs,” not to mention (6) “Leap-frog Logins,” when a user logged in from one monitored computer to another and may gain unauthorized access to a second computer via the permitted access of the first computer, and finally the (7) “Remote Access Sessions” showing users who are not authorized to access other computers remotely.
To learn more about all of our special features, including the top 5, you can visit our features page or contact meand I can give you a quick demo.
Subscribe to the Proofpoint Blog

