Like it or not, your greatest risk already has access to your critical data and systems and it comes from your employees, privileged users and authorized vendors. When trusted users with access to key systems and data are careless, become compromised, or have malicious intent, confidential, proprietary data can quickly become exposed.
Detecting insider threats, however, can be challenging for organizations due to the combination of limited, or no, visibility into user activities. Since privileged users, business users and vendors have legitimate access to valuable information, it can be difficult for organizations to differentiate between appropriate activities and a true insider threat incident.
These 7 steps will help you detect and prevent insider threats:
-
Monitor all user access to data
Increasingly, we are hearing from our customers that monitoring “privileged” users is a thing of the past and that to truly address insider threat, all users with access to systems and data such as CRM, finance, HR, legal applications, databases and network files should be monitored. By monitoring who, did what, where, and when, and identifying and isolating abnormal behavior, you can evaluate risk tolerance and respond quickly and appropriately.
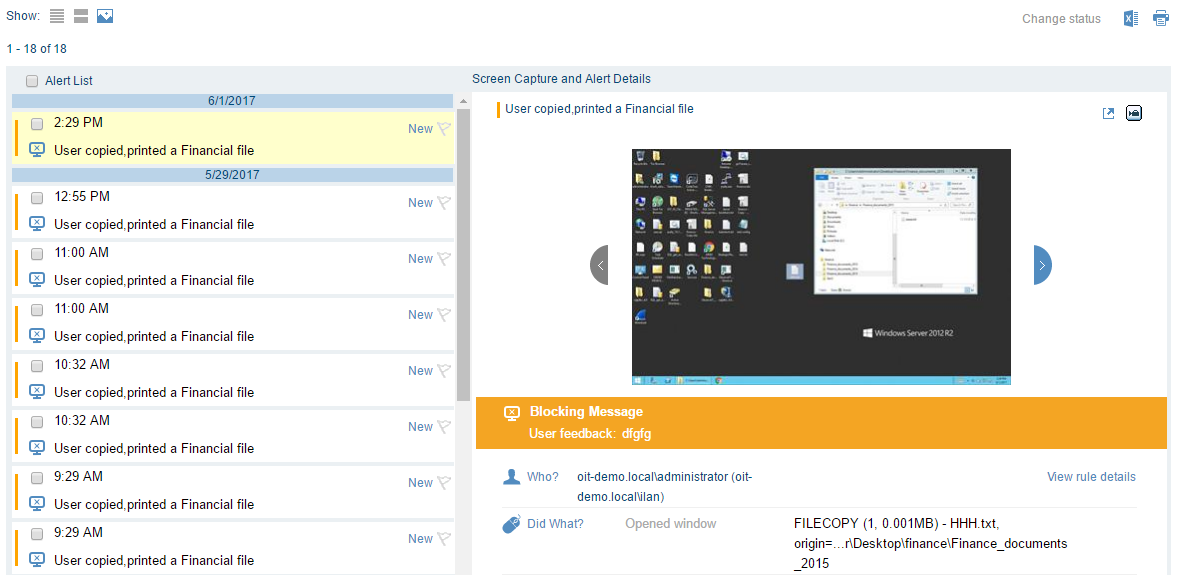
2. Define and enforce organizational policies
Policy enforcement allows you to immediately prevent unwanted data access behavior and enforce separation of duties. Policies should cover both security and compliance requirements with the flexibility and scalability that matches your needs. With an easy-to-use policy management system, you can process rule sets across data repositories.
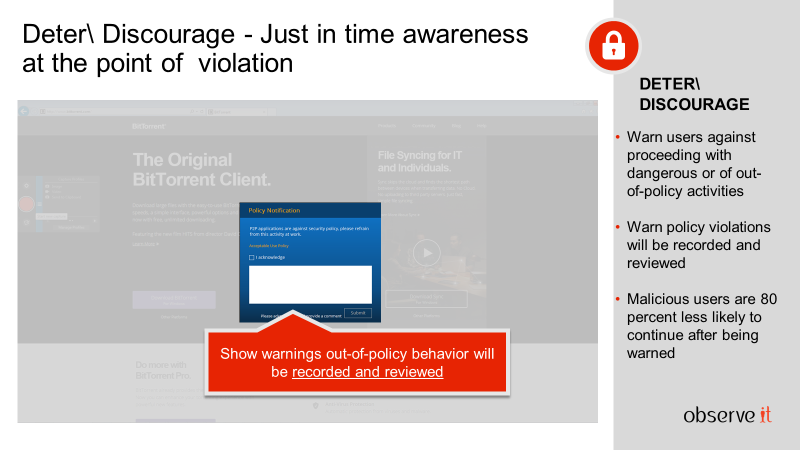
3. Leverage advanced user analytics to detect unknown threats against enterprise data
Proofpoint ITM provides visibility into a risky user profiles in order to investigate and view aggregated information about the user's activities, such as:
- Where do users spend most of their time?
- Which applications are they using?
- How much time do users spend in applications?
- In which sessions were specific applications used?
- Are any suspicious computers or accounts being used?
- Does a user's behavior seem abnormal?
- Does a user's behavior appear different to their peers' behavior?
- How much time during working hours is the user idle?
User Activity Profile information enables you to see the context of a risky user's activities – what they did before, during and after an incident - enabling you to identify insider threats more easily.
4. Use insider threat monitoring tools to investigate security incidents
Your security teams should be able to quickly drill down and understand all data access activities of individual users in order to investigate incidents that are identified using real time alert rules. With the right solution, you should quickly investigate and see the full story of what happened before, during and after an incident. With robust metadata and unambiguous video evidence, security teams have the ability to answer who, did what, on which machine, when based on accessing one system rather than spending time sifting through logs and multiple systems.
5. Identify high-risk users
Once suspicious data access incidents are identified, having the ability to drill down into the audit trail to perform forensics then decide whether or not to prevent a user from accessing your Windows Servers, Unix & Linux Servers, Business Applications and even a specific Window within an application. Granular policies allow you to block access to specific data and proactively prevent or contain data breaches.
In Proofpoint ITM, you can use built in user lists and create new user lists:
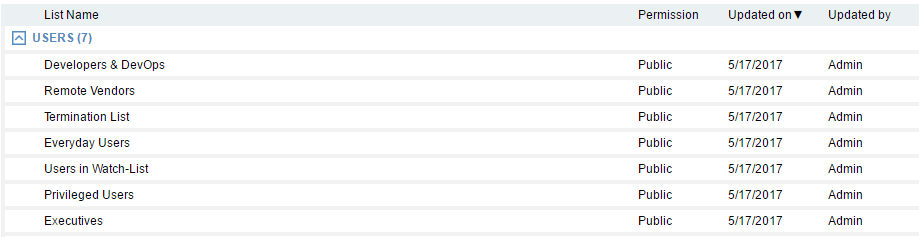
And apply a blocking policy as the example below to prevent “termination list” users from remote desktop access to corporate servers:
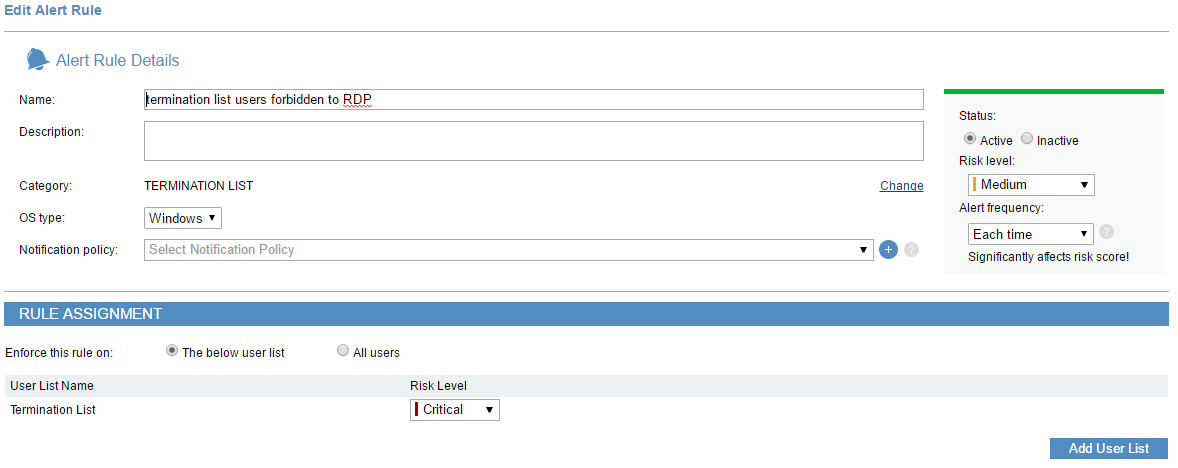
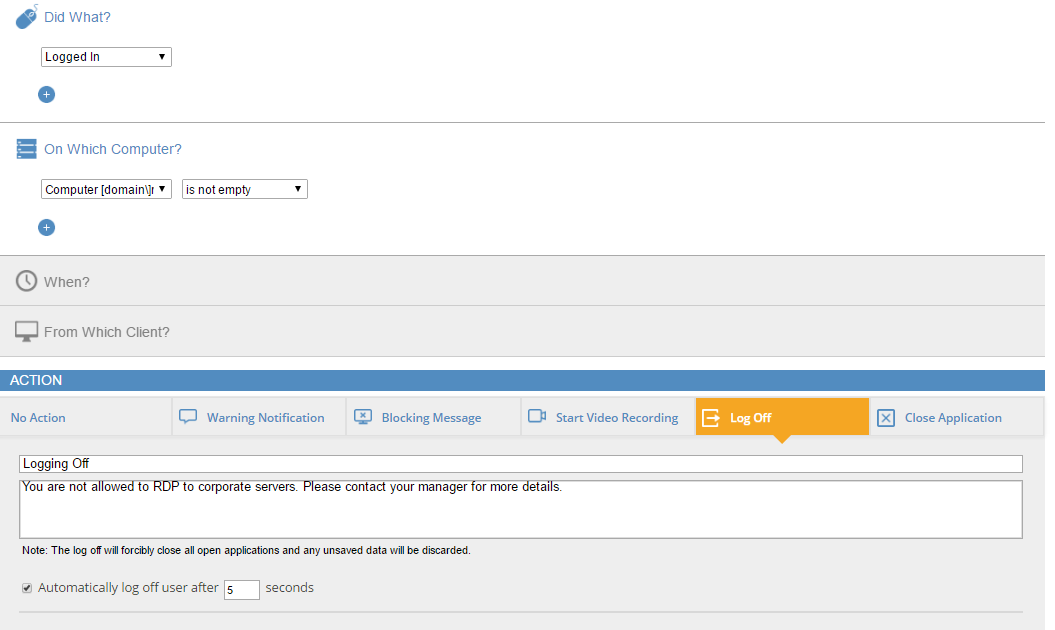
6. Generate reports to document security events
On-Demand or scheduled reporting on all insider-related security incidents provides an understanding of your overall security posture and allows you to provide detailed information to management. In addition to graphical dashboards, pre-defined reports are available in the solution and offer the flexibility to create custom reports.
Proofpoint ITM's unique metadata architecture enables the generation of detailed reports, quickly and effectively. Reporting on alerts and application data fields significantly improves security operations and adherence to regulatory compliance.
Within the Proofpoint ITM Web Console, the reports view provides aggregated or summary information about all monitored Windows and Unix-based endpoints.
The feature-rich report generator can be used by novice administrators to generate reports based on preconfigured built-in reports or by experienced administrators and security auditors who require flexible application usage reports and trend analysis reviews. Experienced administrators and security auditors can also create comprehensive customized reports based on their own requirements.
The following is an example of a typical reports list.
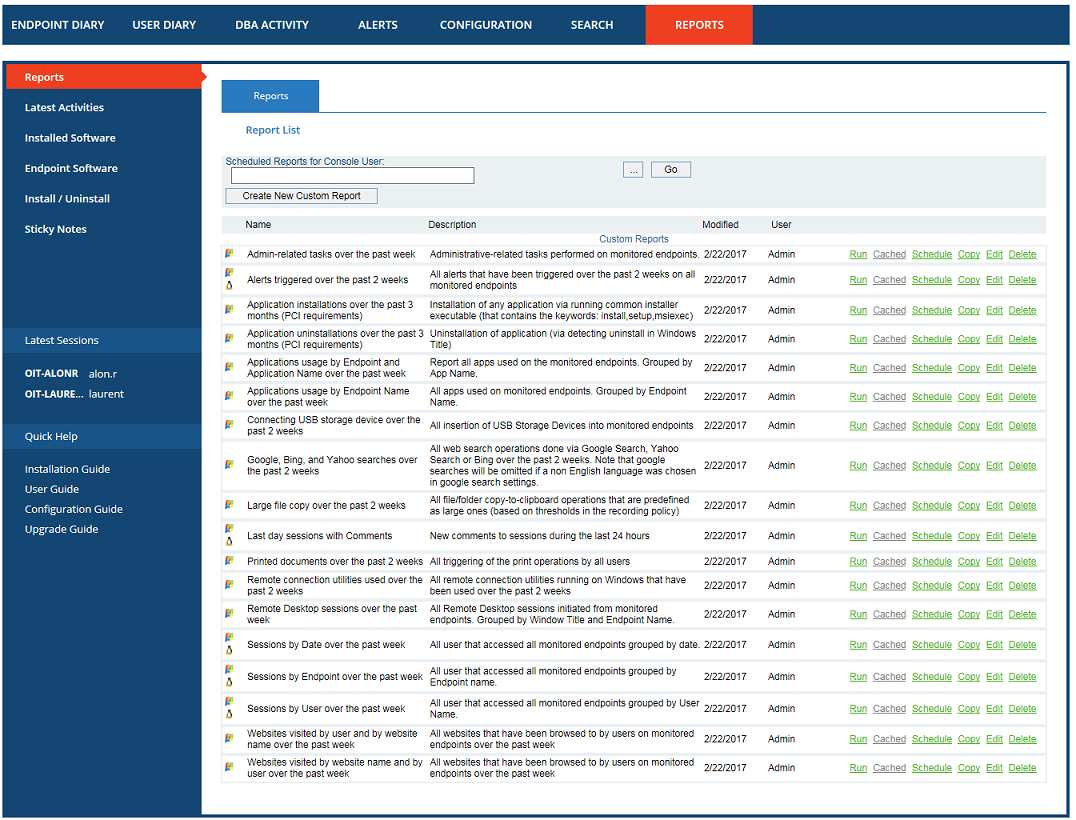
 7. Track data access
7. Track data access
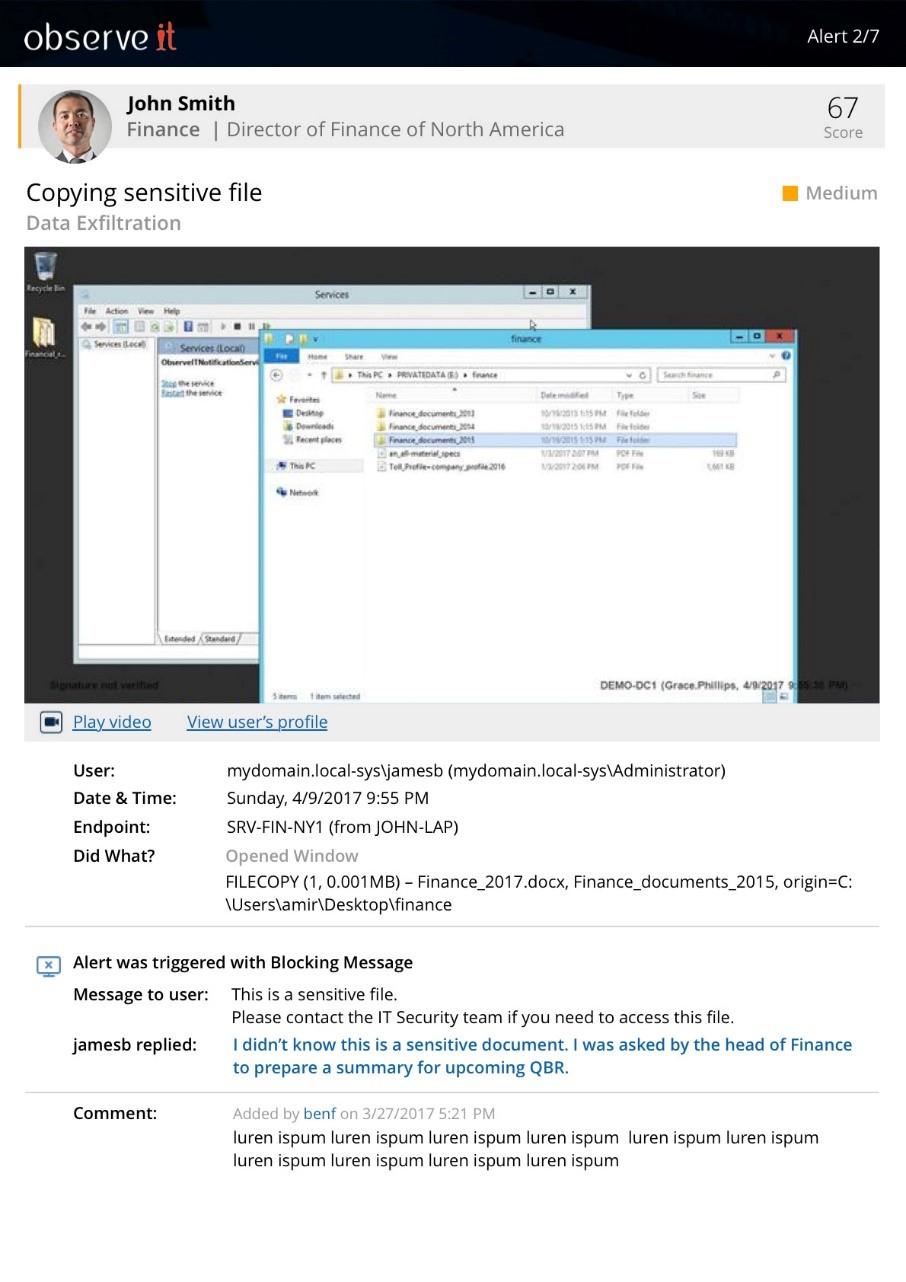
The new Proofpoint ITM File Diary enables administrators to track what users are doing with data. This feature helps detect data theft, provides a user and data activity summary of exactly what happened, and helps counteract some of the most common ways users attempt to export and transfer sensitive data out of the organization.
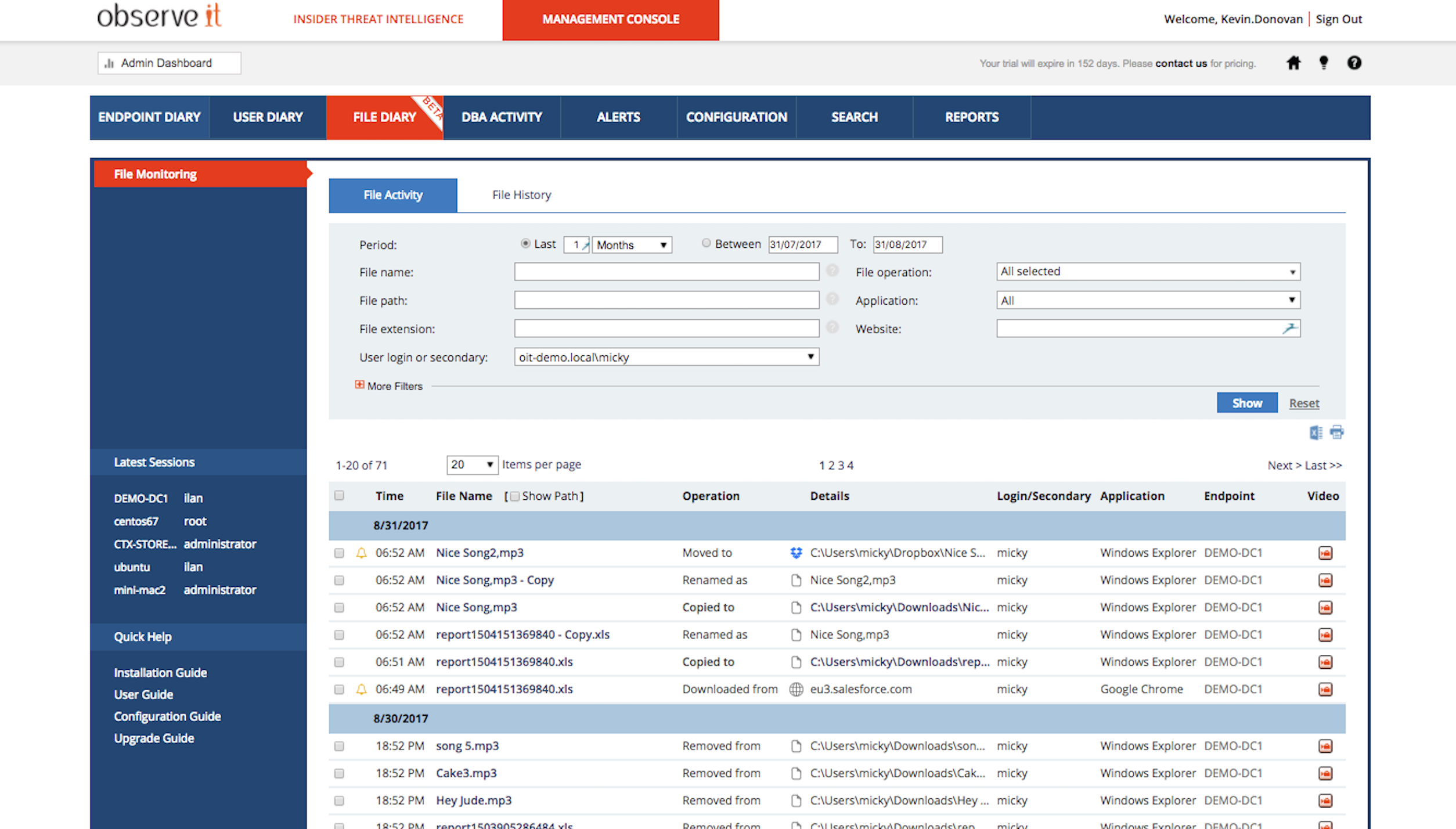
This feature allows administrators to view the life cycle of a user interacting with file. For example, we see this user downloaded a sensitive file from a web repository, moved it from the download folder to the desktop, renamed the file, and then moved in to their personal drop box. The feature was designed to provide visibility on users that download specific files from websites or web applications, whether on the internet or in the local intranet. Proofpoint ITM tracks files accessed and then alerts administrators when a tagged file is moved to a local cloud sync & share folder, such as Dropbox. Furthermore, copying to the clipboard text from sensitive applications can now be tracked and alerted on, providing administrators with additional detection visibility on potential data leaks. During an incident, this level of granularity is crucial in the investigation process and proves that stringent controls are protecting the organizations data.
Proofpoint’s mission has always been to help organizations identify and eliminate insider threats. Ensuring data doesn’t leave the organization’s walls maliciously or accidentally should be a key component to any insider threat program. Take Proofpoint ITM 7.1 for a test drive today and see how Proofpoint ITM helps security teams detect insider threats, streamlines the investigation process, and prevents data exfiltration.
Subscribe to the Proofpoint Blog

