(Updated on 10/11/2020)
In a privilege escalation attack, the attackers can elevate their privileges by granting themselves authorizations that are usually reserved for higher-access users. In most privilege escalation attacks, the hackers first log in with a low-end user account and then searches for exploitable programming errors or design flaws in the system that can be used to escalate their privileges. If the hackers successfully exploit such vulnerabilities, they may create new system users, access files, authorize network activity, and change system settings. Such an attack can result in the theft of sensitive data or the hijacking of an entire network.
Proofpoint Insider Threat Management (ITM) Detects Privileged Escalation in UNIX
ITM is a user-activity monitoring security software that provides the alerting required to detect privileged escalations in UNIX. ITM also employs screen recording technology to capture privileged user activity such as privileged escalation, regardless of the environment and converts the screenshots into User Activity Logs which makes searching, analyzing, and auditing user activity simple and easy.
7 Ways To Detect Privileged Escalations in UNIX
Please see below 7 ways privileged escalations can occur in UNIX and how ITM can help organizations protect themselves against each one of them.
1) Sudo into root shell - A sudo allows an admin to delegate authority to give selected users the ability to run commands as a root or another user. ITM alerts if someone is running a sudo command to interactively open a root shell that does not require a root password. Traditionally, it is difficult to track user actions because in shell you are not limited to a specific command but with ITM it’s simple. (See Exhibit 1)
2) Update root cron jobs - A cron is a time-based scheduler program that enables UNIX users to automatically execute commands or scripts at a specific time and date. Cron jobs are used for scheduling tasks to run on the server. ITM alerts when the –e option is used with root permissions to modify cron jobs that will later run with root permissions, enabling potential backdoor user activity at a later date.
3) Edit sudoers files - The sudoers file controls who can run specific commands as specific users on specific machines and can also control special actions like whether you need a password for particular commands. ITM alerts when the sudoers file is edited, as this could enable unauthorized root permissions for the user.
4) Changing a program to a setuid programs (possible backdoor) – Setuid short for “set user ID upon execution” are UNIX access rights flags that allow users to run programs with temporarily elevated privileges in order to perform a specific task. ITM alerts when a user tries to change a program to a “setuid” program (which automatically provides root permissions while the program runs), since this could enable potential backdoor user activity.
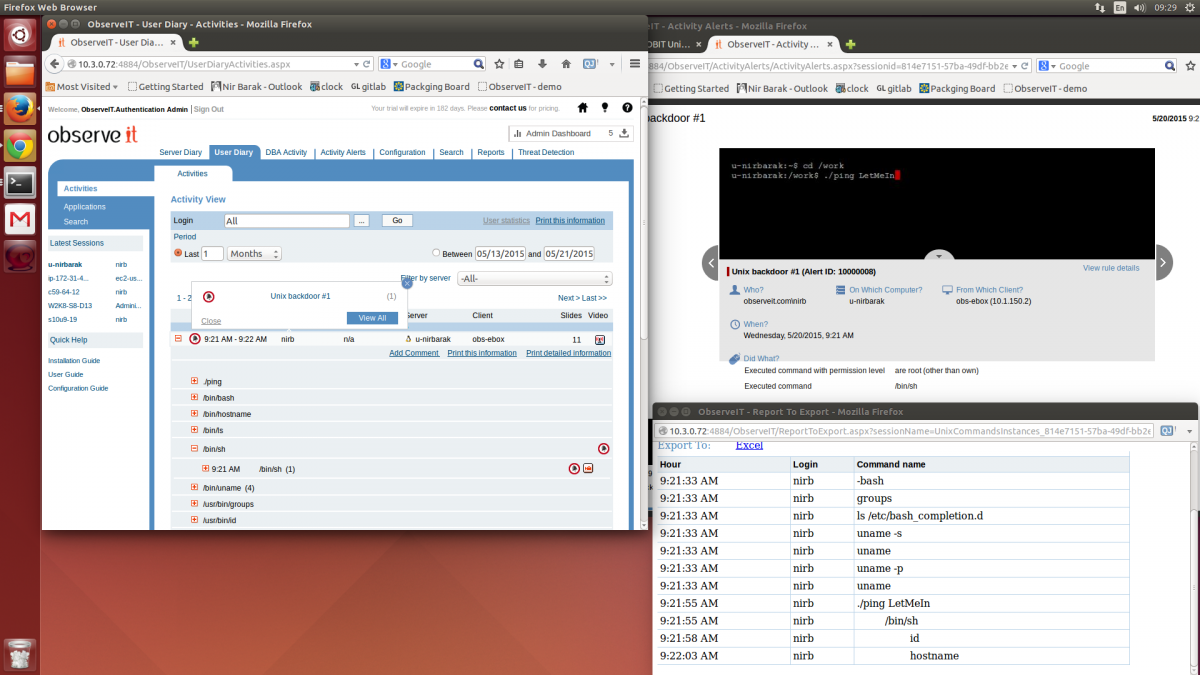
5) Opening generic root shell – Root shell is one of the main targets of hackers since they can then run whatever command they want, under full authority and it is very hard to track what they do when they get it, ITM can track when a regular user opens a root shell so it can be monitored to make sure is a legitimate action, and commands done under the sensitive shell can be monitored. (See Exhibit 2)
6) Creating local user with duplicate user ID - ITM alerts when a user with privileged permissions creates a new user with the same ID as an existing user. The newly-created user could login with his/her own password and perform actions as if they were performed by a different user (especially suspicious for power users like root).
7) Su into root shell with no password - In UNIX, the “root” user has control over the machine. An attacker will want to obtain a shell prompt so that any command can be entered that will execute with root privileges. ITM alerts when a regular user runs a program that opens a root shell using "sudo su". The user will not be asked for the root user password and will have root user permissions without knowing the root password.
Final Thoughts
There are a variety of ways that an attacker can escalate privileges in UNIX and the outcomes can be extremely detrimental resulting in the theft of sensitive data or the hijacking of an entire network. This is especially true if the attacker creates new system users, accesses files, authorizes network activity, and changes system settings. With ITM's alerting capabilities, organizations can protect themselves against privileged escalations and keep their sensitive data and network safe from harm's way.
Learn more about ITM's insider threat management solution can help you prevent and detect insider threats effortlessly.
Exhibit 1: Sudo into root shell
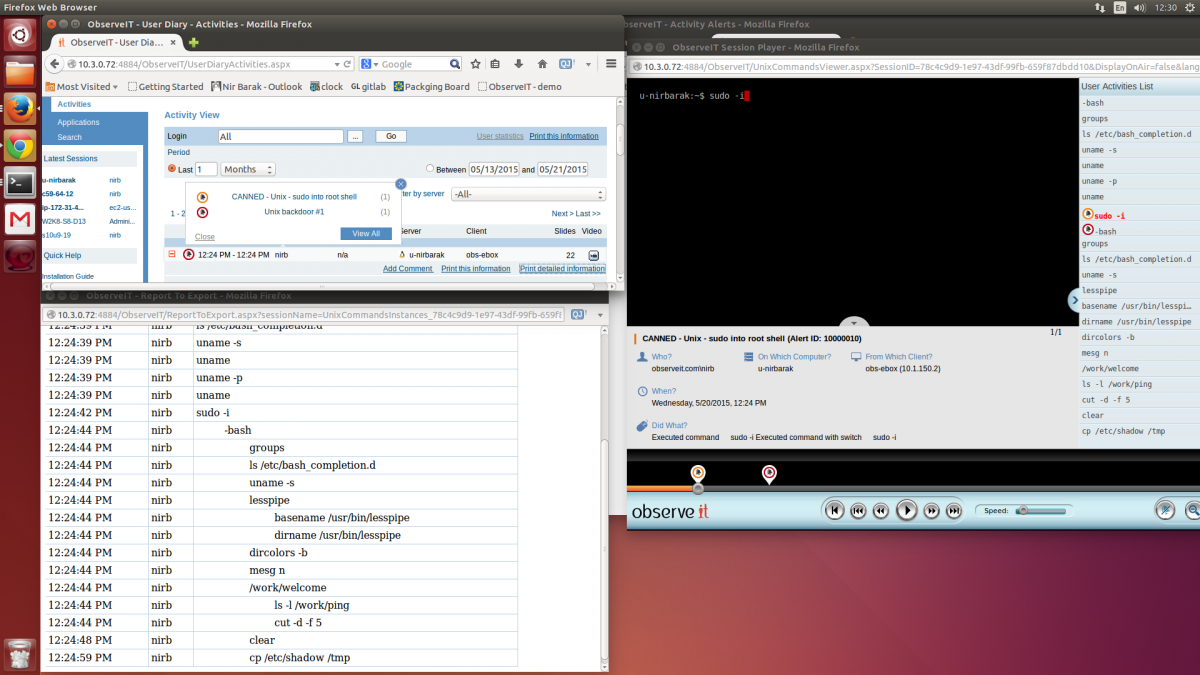
Exhibit 2: Opening generic root shell
Subscribe to the Proofpoint Blog

