(Updated on 02/22/2021)
Email is a common exfiltration point for important data. Employees may send confidential information via email clients, send attachments including important documents or images, or save attachments with sensitive information to their computers and later exfiltrate it.
Proofpoint ITM 7.8 introduces increased visibility and detection of data exfiltration via email clients. The new email exfiltration features monitor email clients on Mac and Windows endpoints, granting comprehensive visibility into user and data context around the sending and receiving of sensitive files over email. This provides important threat protection capabilities for this popular method of corporate data exfiltration.
Detect, Investigate, and Respond Faster to Email Exfiltration
Proofpoint ITM’s new data exfiltration features enable the security organization (or any other relevant stakeholder within a company) to detect, investigate, and respond faster to users who inadvertently or intentionally exfiltrate sensitive data over email, by setting up email monitoring policies and alerts.
This new visibility covers any emails sent to external or internal recipients via Outlook (on Windows or Mac) and Apple Mail email clients, with or without attachments. Security admins can now view and alert on any potentially risky email to detect exfiltration. Teams have a great deal of flexibility to determine what types of emails to monitor and what alerts they want to receive.
Using Proofpoint ITM 7.8, teams can detect email exfiltration at multiple stages based on different types of events, including:
- When a file is attached to an email
- When the email is sent
- When an attachment is saved to disk
Now that you understand the basic capabilities of these new features, let’s look at the different ways you can access and process the information.
Email Diary
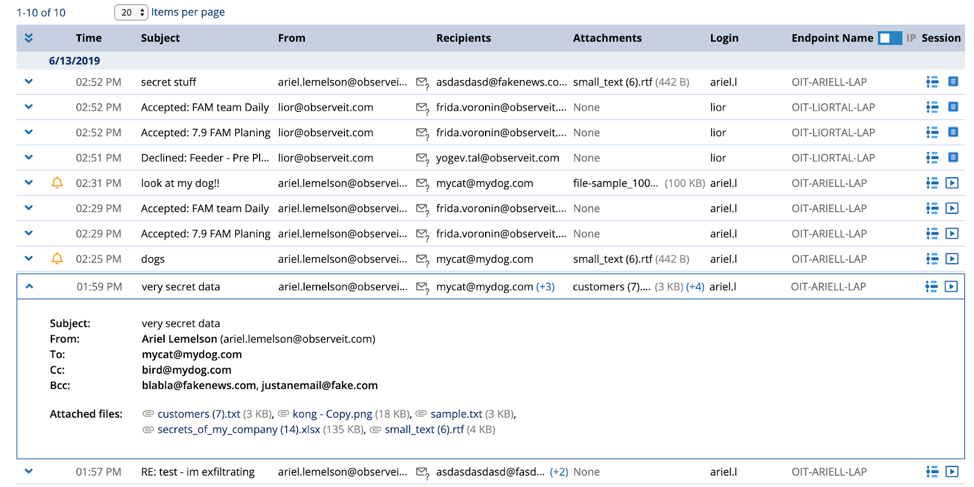
From Proofpoint ITM’s email diary screen, security admins can review and filter monitored emails. This can help them detect and investigate sensitive data exfiltration via the company's email client. Significant information about each email can be consumed and viewed in just one screen (the email diary) on the Proofpoint ITM platform, including:
- Fields: from, to, cc, or bcc
- Subject
- Attachment name and size
- Recipient’s domain classification (trusted/untrusted).
This consolidated visibility enables much faster investigations. Proofpoint ITM also provides easy navigation to continue diving deeper into context within each user’s timeline. In the email diary view, admins can also view emails sent by high-risk users with or without attachments.
Granular Email Monitoring Policies
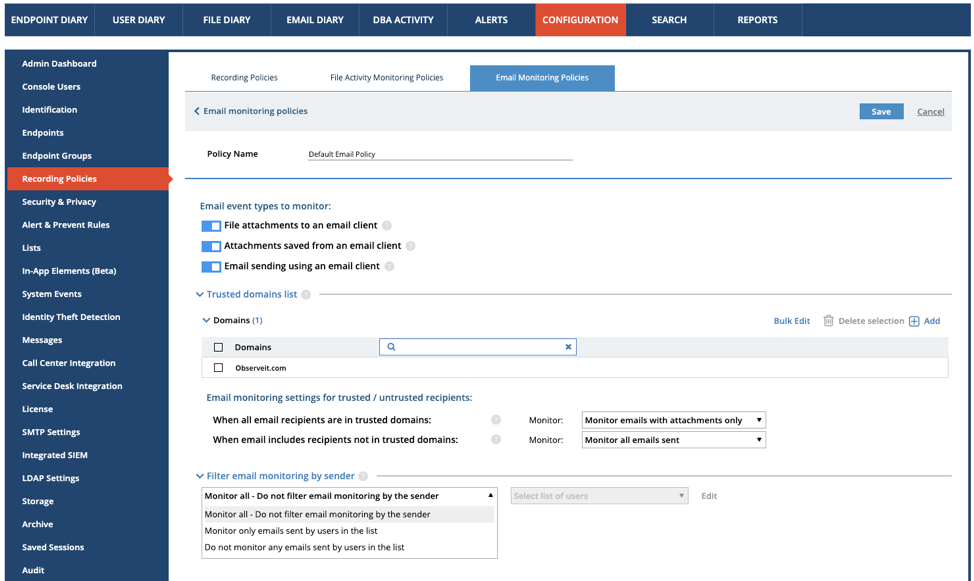
By default, when email monitoring is enabled, all emails sent via an email client, any files attached to an email, and any attachments saved from an email are monitored. That said, to use Proofpoint ITM’s email monitoring features efficiently, admins may choose to alert on specific email activity that matters to the organization—such as emails sent to recipients outside the company via the internal email client or emails sent with attachments only. Granular email monitoring policies let admins define which emails to monitor.
Email monitoring policies can be defined by one or more of the following:
- Email Events: Monitor specific event types, e.g. sending emails, attaching files or saving attachments.
- Internal vs. External: Easily distinguish between internal and external emails and set policies to treat the different types accordingly
- Recipient's Email Domain: Monitor emails by recipient domains, which can be defined as trusted/untrusted.
- Sender: Monitor emails only if sent by a certain list of users or if sent by anyone except a certain list of users (Note: This feature supports Active Directory lists). Examples of these lists could include privileged users or high-risk users.
Some organizations may want to monitor small groups of individuals that are considered high-risk while ignoring email sent by the rest of the users. Other organizations take the approach of monitoring all outbound emails and only excluding a list of sensitive users from their email monitoring.
With Proofpoint ITM, organizations have a high degree of control over what their email monitoring policies look like and how to implement them.
Granular and Comprehensive Email Activity Alerting
Security admins can also define alerts so they are notified when one or more of the following occurs:
- Suspicious emails are sent
- Files are exfiltrated by sending them via email
- Sensitive attachment files are saved from an email that is received
- A sensitive file is attached to an email
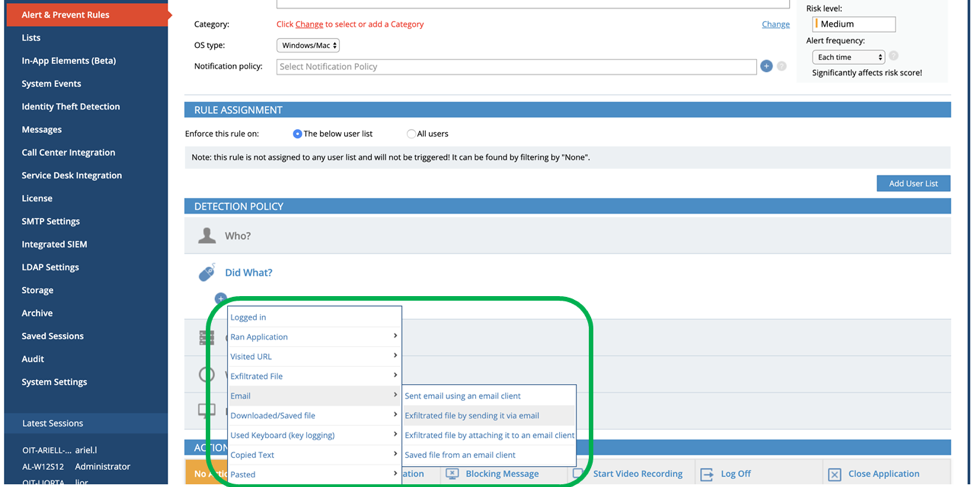
Inside each of the above categories, there is a huge variety of conditions that can be set around sender and recipient info, including:
- Domain (e.g. sent to a competitor’s domain or an untrusted)
- Attachment details (e.g. number, names, size)
Attachment detail alerting can also be used to receive alerts when, for example:
- An email is sent with more than 10 MB of attachments to an untrusted recipient
- An attachment contains sensitive keywords in the name
- An email contains sensitive keywords in the subject
- Sensitive directories are involved
- File history indicates risk
This enables a broad range of use cases and deep customization. Such flexibility in alerting allows “finding a needle in a haystack,” while keeping the noise to a minimum.
Tracking File Movement from Emails
Finally, teams may want to track a certain file before and after it leaves the organization via email. With Proofpoint ITM, teams can monitor valuable information that users receive by email during the file’s lifecycle—tracking renaming, copying, and exfiltration. Security admins can also track files downloaded from the web and then exfiltrated through email. This, again, enables them to develop a bigger picture view and more context around what happened and why.
Common Use Cases for Proofpoint ITM 7.8
Here are some of the most common use cases for our customers including detection and investigation of:
- Emails sent to competitors’ domains which contain attachments
- Emails sent externally that contain more than 5 MB of attachments
- Emails sent externally that contain attachments with sensitive file names
- Emails that contain sensitive keywords in the subject
- Emails which contain “bcc” recipients
- Emails sent by high-risk users for data exfiltration or suspicious usage
- High-risk users exfiltrating sensitive data outside the organization
- Users sending and receiving sensitive data to and from unauthorized domains
- Files downloaded or saved from corporate emails and exfiltrated through other channels
You Can’t Turn Off Email
Many of our customers worry about data exfiltration via their email clients, and for good reason. Of course, companies can’t simply shut down email to stop this common exfiltration point, since it is such a key part of employees’ day-to-day workflows.
Previous controls available to monitor email lacked context, visibility, and control over alerting and investigations. With Proofpoint ITM 7.8, customers now have access to this key information, correlated with user and data activity. The new features provide context in a quick-to-consume, friendly workflow. The flexible configuration and alerting options allow efficient detection and investigation efficiently. All of this helps the security organization and the entire business gain the upper hand against email-based data exfiltration threats.
New to Proofpoint ITM?
Subscribe to the Proofpoint Blog

