(Updated on 02/22/2021)
It happened again…
Your trusted business partner was granted access to your internal file-share and began pulling gigabytes of data to their corporate-issued laptop. You’re safe, right? All the discovery was done, the files are tagged, you know who has read and write permissions on the Share. Your network and endpoint DLP are patrolling the virtual corridors like watchdogs—if the data moves, you will know.
Then why do CISOs still identify data exfiltration as their biggest concern? A survey of more than 1,500 security professionals found that data exfiltration from an endpoint is the top security concern of 43% of them.
CISO, global financial services companies: “I haven’t seen a data loss prevention tool my team can’t bypass in two seconds.”
In recent years, tools such as Data Loss Prevention, Database Activity Monitoring, Network Share Monitoring and Data Discovery Platforms have become common best practices and gold standards for IT Security teams. Compliance teams check boxes and thousands of hours are spent responding to alerts. But despite these developments, one major blind spot remains: the use and misuse of unstructured data on an endpoint. Once a file has left the monitored confines of Net-Share, Sharepoint, Onedrive or Salesforce, the ability of an Information Security Analyst to identify abuse of file access drops dramatically.
The issue is a lack of necessary visibility to effectively detect and respond to the event. An analyst who receives an alarm (if she’s lucky) from a DLP must now spend hours correlating that data with other systems. She must rely on DNS logs, Exchange logs, access rights from the Net-Share, website access reports, and email correspondence reports. By the time the analyst finishes her investigation she has a mile-long data trail that still does not tell her—with confidence—what the business partner did with the data or why.
The problem exists because the analyst is looking at system data to tell a security story about a user. The answer to this problem comes by understanding user context with comprehensive accuracy.
Proofpoint ITM File Activity Monitoring vs Data Loss Prevention
In almost every case, customers who use Proofpoint ITM already have a DLP system. In nearly every situation, we find DLP is either not performing as intended or its capability is stretched outside of the original project scope.
The core value of a DLP is its content analysis capability: to dig into a file to verify its content. DLP systems can be incredibly powerful, but with great power comes a significant amount of customization and configuration. Proofpoint ITM, on the other hand, doesn’t focus on the contents of a file or repository to provide value. Proofpoint ITM combines user generated events and file activity data to indicate the potential of a security problem , insider malfeasance, or benign error.
DLP systems are known for being overloaded with data; however, answers to questions such as “Who moved my source code and to where?” or “why did 30 GB of data go to the contractor’s Macbook?” or even “what files did Alice take on her last day?” remain elusive when using these systems.
CISO, global investment firm: "After spending 3 days investigating an incident I realized that our DLP wasn't "Protecting" anything"
A DLP struggles with presenting its findings and data to a business team without painstaking translation and correlation by Information Security teams because it was not designed with these questions in mind.
Customers turn to Proofpoint ITM to provide instant context where a DLP cannot go; to validate incidents, accrue forensic data, and verify the alarms generated by a DLP. In some cases, Proofpoint ITM is preferred if a DLP is deployed only to the perimeter, clumsily maintained, or has been removed due to performance costs on critical machines.
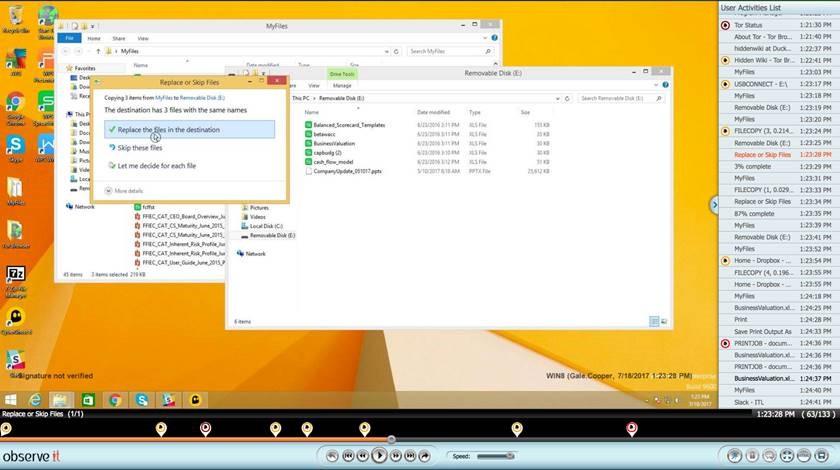
The biggest benefit of Proofpoint ITM: dramatically less effort for a simple audit trail of a user’s application, file, internet, and window activity so that you can very quickly understand user activity without having to wade through the noise. Stop using rigid data monitoring rules and policies on humans who are by nature flexible and unpredictable.
As you can see, tying users to activity, combined with the capability to alert or block based on flexible policies, makes Proofpoint ITM interesting. Imagine being able to kick off a security investigation based on many file downloads, a website being accessed, or a specific time-frame—then seeing what happened before and after the event.
Proofpoint ITM and DLP work extremely well together, but each provides plenty of value on its own. Get a DLP to check a box, use Proofpoint ITM to tell a better security story.
Subscribe to the Proofpoint Blog

