This is the true story of how User Activity Monitoring helped prevent a senior IT administrator in a major telecom company from stealing customer data to sell to competitors, and credit card numbers to sell to players in black market cyber-bazaars.
This IT administrator, who has been at the company for about two years, was responsible for database and storage management, reliability and optimization. His role required unhindered access to all of the company’s databases, giving him the means and opportunity to steal sensitive and valuable data.
This IT administrator was also well-aware that Proofpoint ITM was deployed and recording all user activity on the servers containing the data he wished to pilfer. Therefore, the first step he took in his attempted heist was to kill the recording agent process on the computer he wanted to use.
During the next 20 minutes, he was able to extract a large quantity of sensitive data and upload it to a personal cloud storage account (Dropbox):
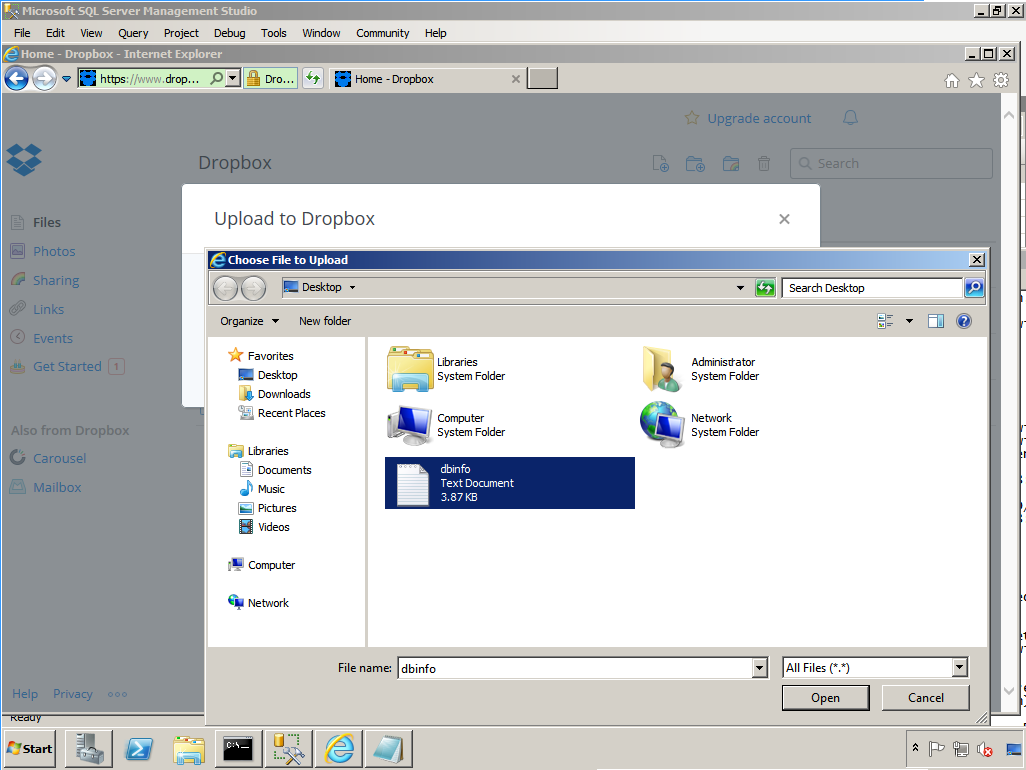
What the administrator did not know (or think to double-check) was the fact that Proofpoint ITM’s “watchdog” mechanism detected the killed agent process and restarted it within 30 seconds. So, everything the administrator did was still recorded and logged.
The following day, a routine review of the Proofpoint ITM event logs by a security administrator revealed that the recording agent process on a particular machine was unexpectedly stopped and restarted the previous day at 9:07 AM:
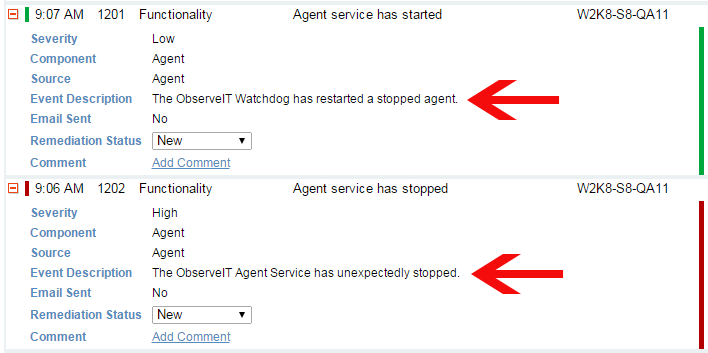
Suspicious about that unusual event in the event log, the security administrator investigated what activity occurred at that server at the indicated time, first by quickly reviewing the user activity logs. He noticed the use of Dropbox, a cloud storage app unauthorized for use on the sensitive database server:
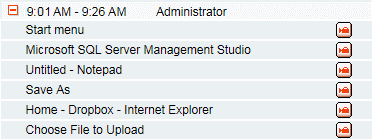
The security administrator launched the screen video recording of that session to see more clearly what the database administrator was doing during that session. Sure enough, the session video playback shows exactly what he had been doing – extracting data from the database, saving it into a text file using Notepad, and uploading it to the cloud:
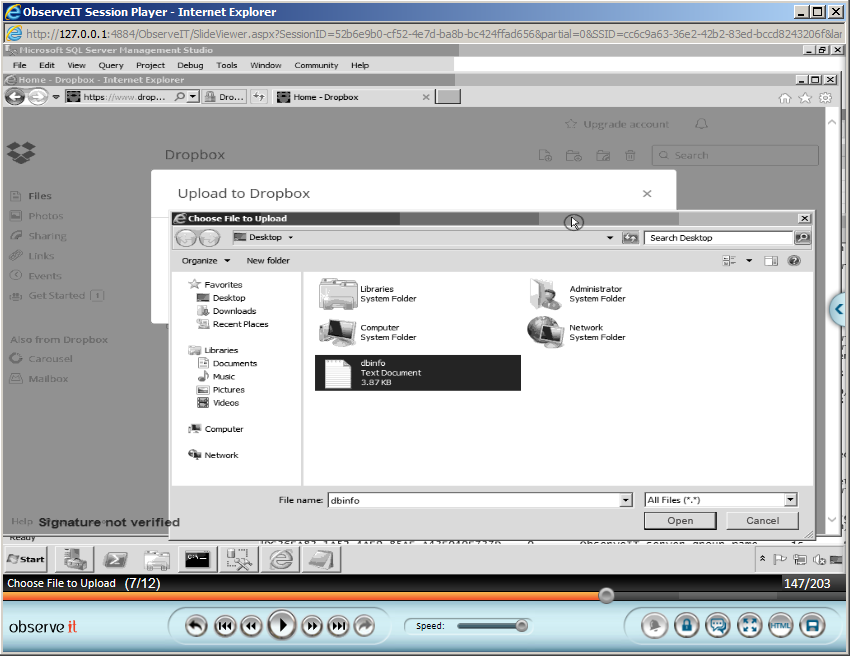
The security administrator immediately downloaded the video showing the extraction and uploading of the customer and credit card data, and sent it to the company’s CISO. This set a process into motion, culminating in the termination of the thieving administrator and subsequent criminal prosecution. The case is still in the courts today. The Proofpoint ITM video recording of the administrator’s actions has already been admitted by the court as evidence for the prosecution.
I suggest that all IT security officers take heed of the lessons learned from this incident:
- User activity monitoring directly prevented a damaging data breach.
- Security systems require redundancy in case they are attacked.
- Insider data breaches are far less likely to occur when users know they are being recorded.
- User activity recordings can be used as evidence in trials (in some jurisdictions).
Join us for a webcast to get another customer’s perspective on Proofpoint. Learn how Xerox leverages User Activity Monitoring to improve business-critical application security. Register here to reserve your spot.
Subscribe to the Proofpoint Blog

