Proofpoint ITM 7.1 takes a big step forward in helping customers detect and prevent data exfiltration.
Many organizations manage confidential or proprietary data in systems accessed via a web interface such as Microsoft SharePoint, Box for Business, Google Suite, and other storage systems. Sensitive data is accessed daily from web/cloud applications such as Customer Relationship Management (CRM), Enterprise Resource Planning (ERP), trading systems, health applications, and other business applications. As increasingly more data is moving to web applications and the cloud, unstructured data sets are growing exponentially presenting a massive security challenge due to the time and effort required to secure it.
Check out the new features we’ve included in the latest version of Proofpoint ITM 7.1 to help organizations prevent the exfiltration of proprietary and confidential data!
File Diary
File Diary enables administrators to track what users are doing with data. This feature helps detect data theft by providing an activity summary with details of both user and data activity. Leveraging this feature provides administrators visibility into some of the most common ways that users attempt to export and transfer sensitive data out of the organization. The feature was designed specifically to provide visibility on users that download files from websites or web applications whether on the internet or in the local intranet.
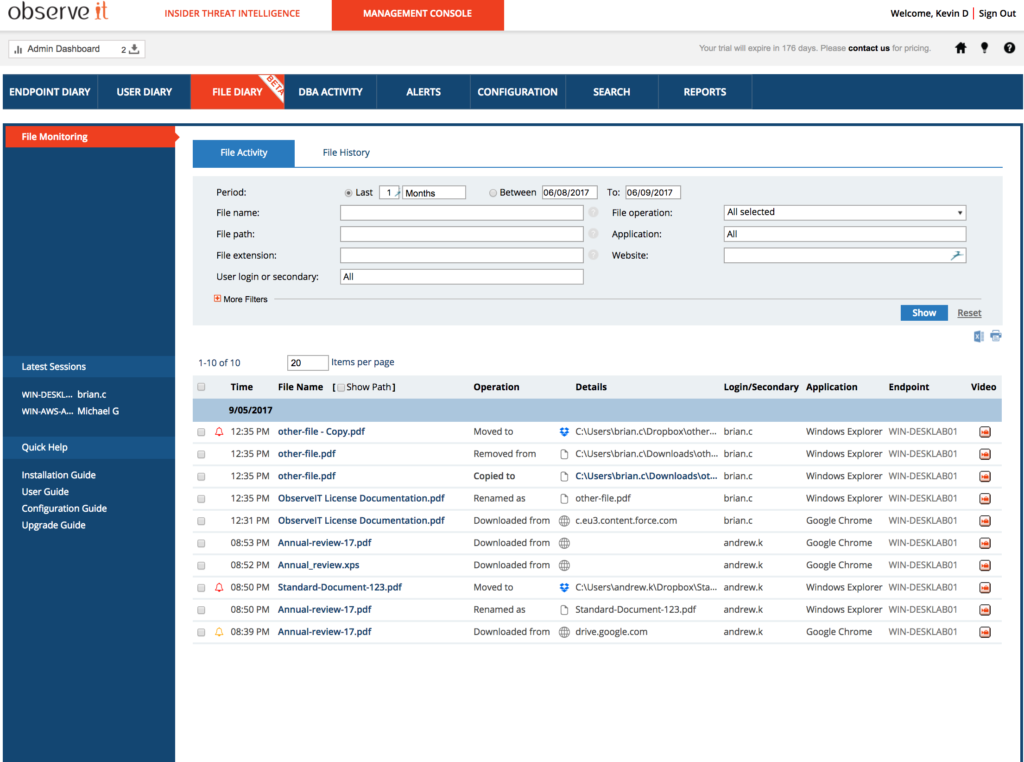
Administrators can view the life cycle of a user interacting with files. In the above example, we can see this user downloaded a sensitive file from a web repository, moved it from the download folder to the desktop, renamed the file, and then moved in to their personal drop box.
How does it work?
Proofpoint ITM tracks files accessed and then alerts administrators when a tagged file is moved to a local cloud sync & share folder, such as Dropbox. You can also track and be alerted when a user copies information to the clipboard from sensitive applications, providing additional detection visibility on potential data leaks. During an incident, this level of granularity is crucial in the investigation process and proves that stringent controls are protecting the organization’s data.
Enhancements Around Incident Response
Proofpoint ITM 7.1 streamlines the incident response process by enabling admins to easily investigate and respond when incident is detected. Security teams and investigators can now view, flag, search, and comment on specific incidents, as well as collaborate with other functions in the organization with comprehensive reporting and high-level summaries.
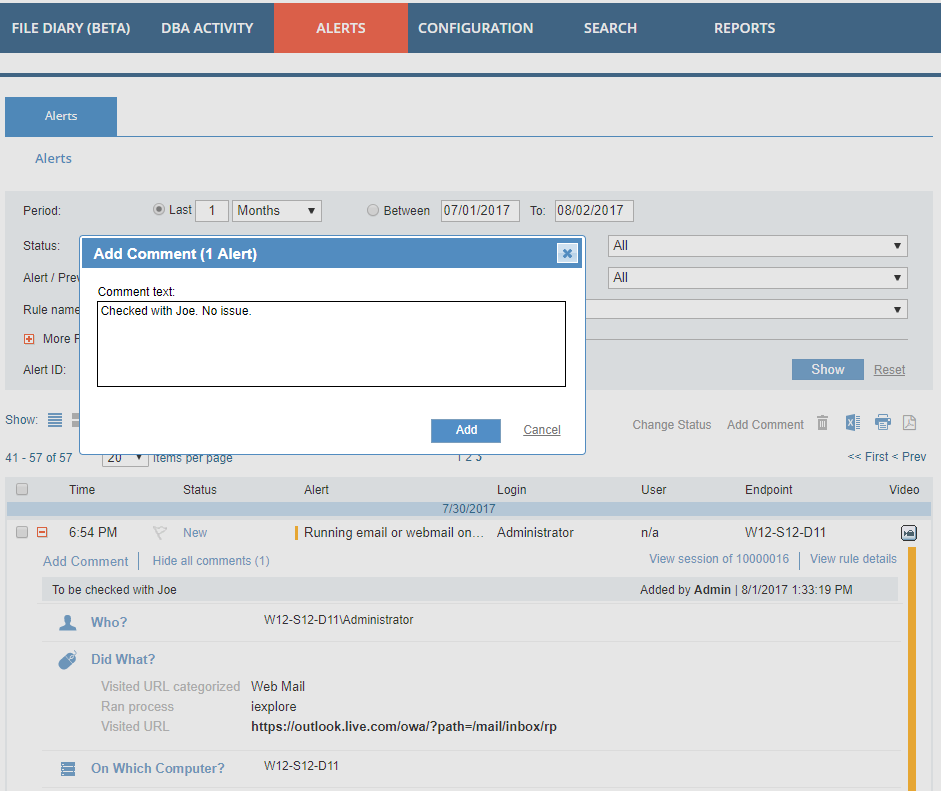
Incident Reporting
Easily export specific information for compliance reporting or generate a one-click user risk summary that displays an incident report of individual users. Additionally, 7.1 new comes with out-of-the-box reporting around alerts, lists, and endpoint information for rapid access to Proofpoint ITM data.
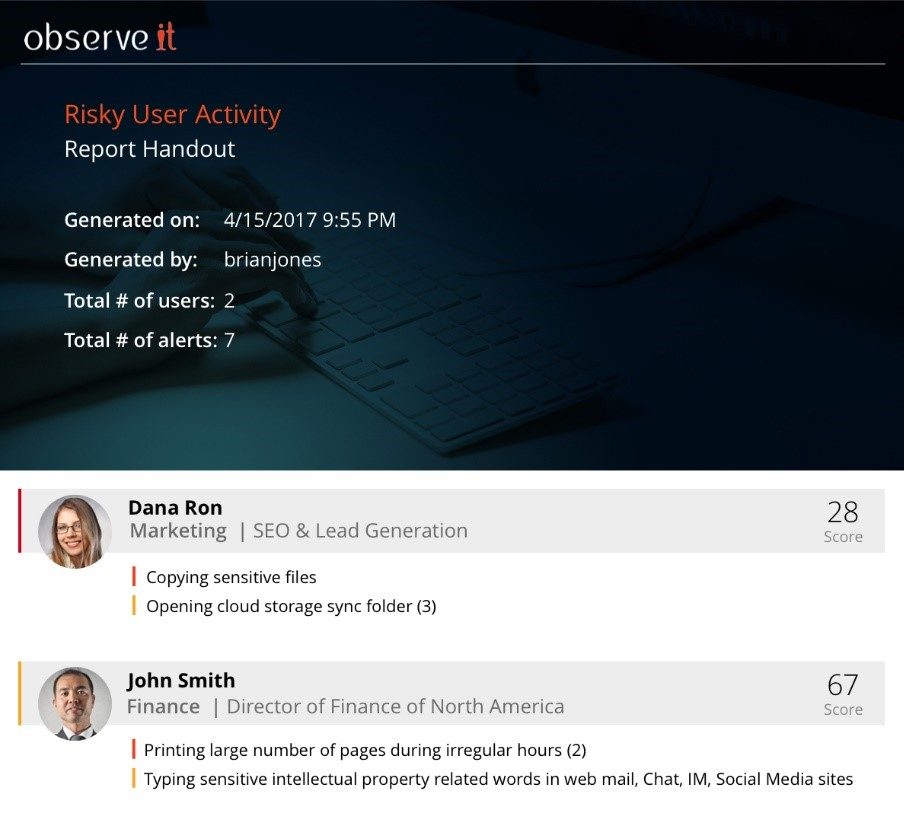
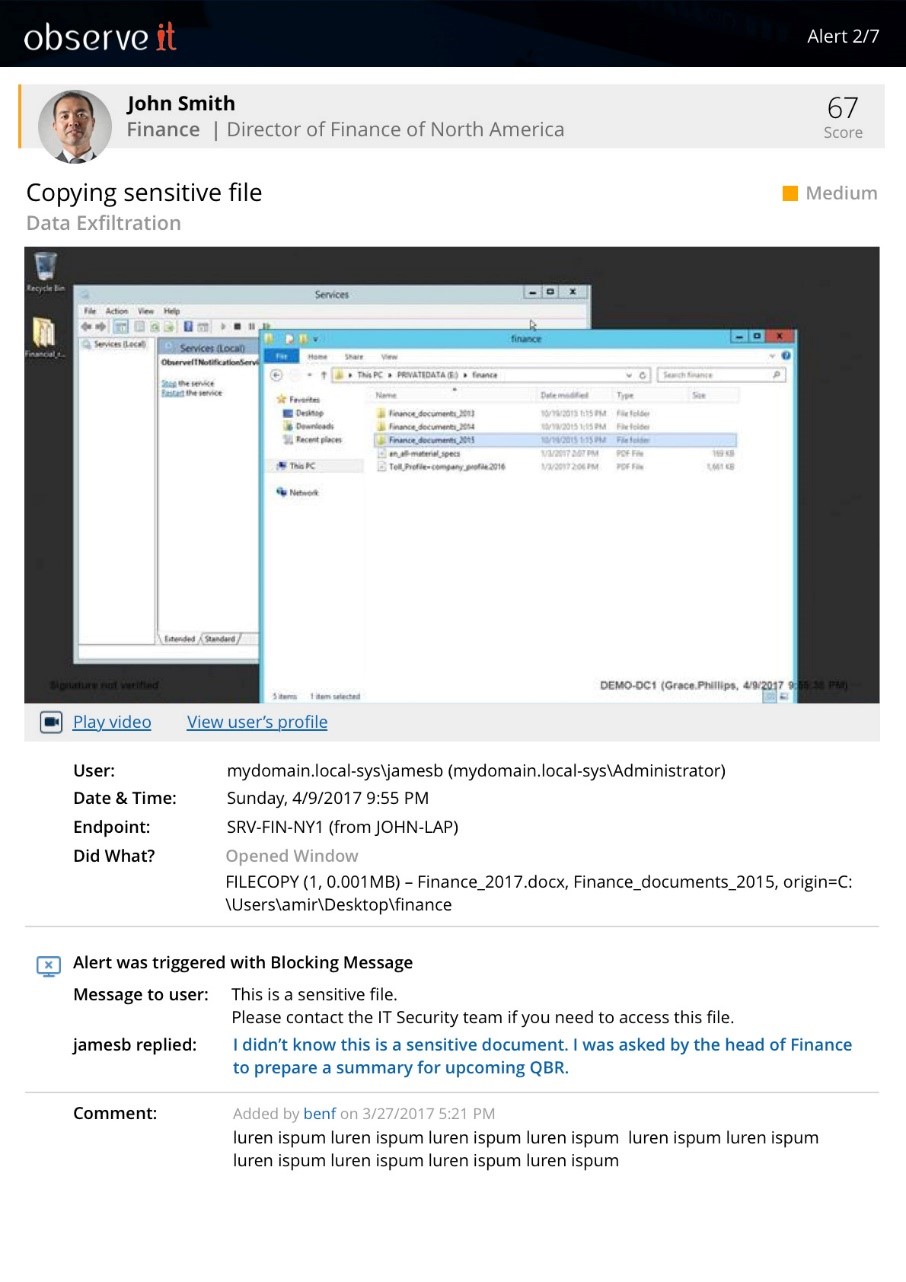
Proofpoint’s mission has always been to help organization identify and eliminate insider threats. We have been hard at work to ensure Proofpoint ITM 7.1 delivers on that goal. Test drive Proofpoint ITM 7.1 today and see how we help security teams detect insider threats, streamline the investigation process, and prevent data exfiltration.
Already a customer? Upgrade Now
Subscribe to the Proofpoint Blog

