Proofpoint ITM has released its next major version 7.0. The company’s mission has always been to identify & eliminate insider threat by focusing on what the user is doing vs what a system or a computer is doing. The 7.0 release reflects this ideology by enhancing its user interface, bolstering its detection capabilities, adding preventative controls, and providing insight with user analytics.
New User Interface
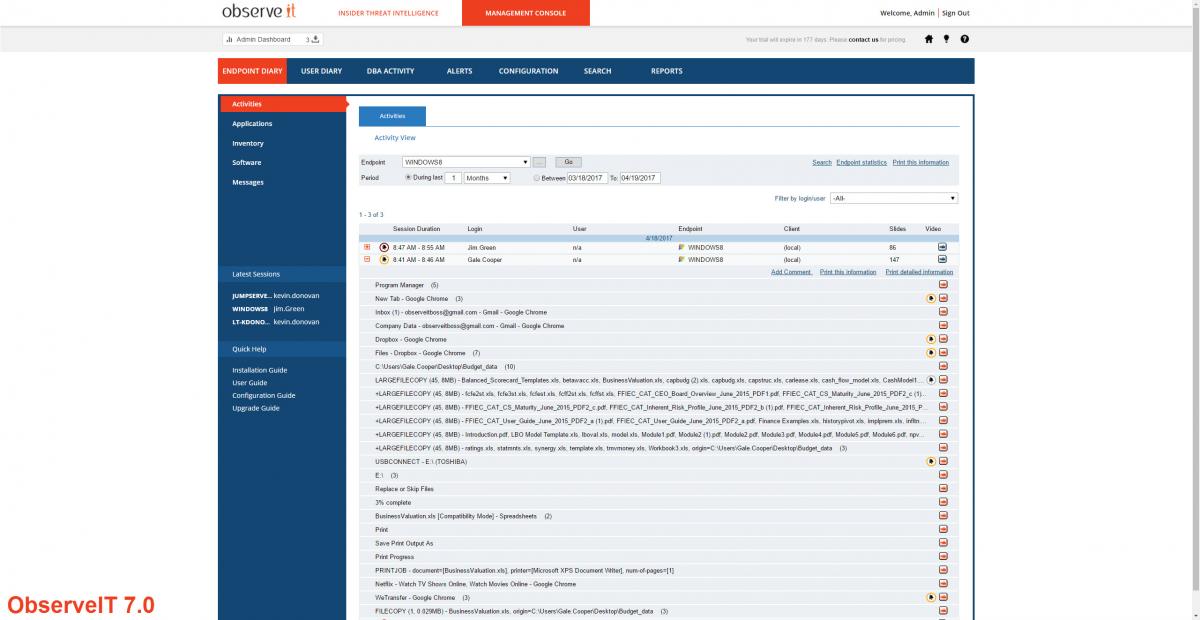
Proofpoint ITM 7.0 introduces a fresh feel and makes the already seamless UI even easier to use. You can now easily pivot between threat dashboards and investigational tools making identifying and investigating user activity more streamlined than ever before.
7.0 User activity feed
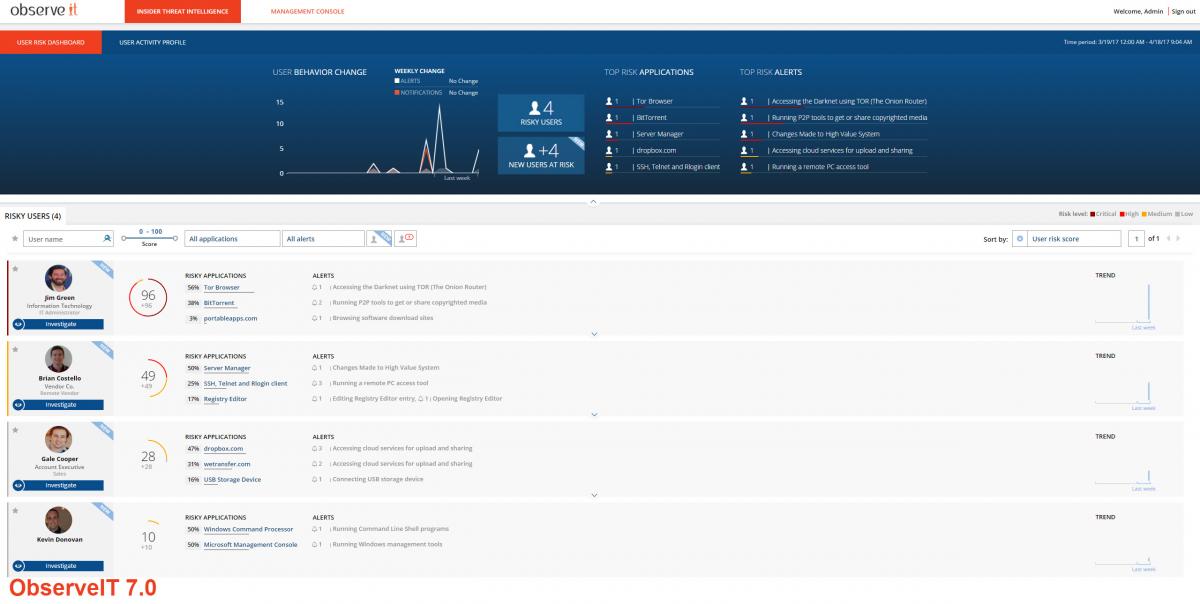
7.0 Insider Threat Dashboard
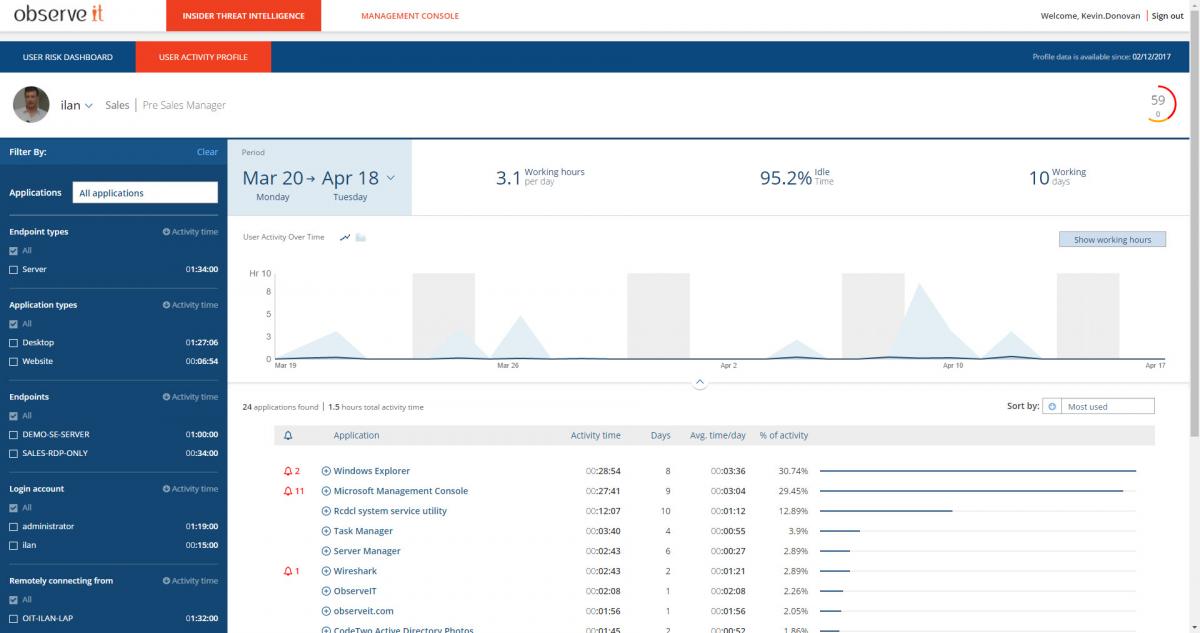
User Activity Profile (UAP)
With the advent of the User Activity Profile, Security and IT teams can traverse the threat landscape of the user's machine by analyzing active time spent on websites, newly installed applications, machine access, account usage, and much more.
This view delivers a better understanding of what users typically do and provides the intel and insights administrators need on specific user activity.
Keylogging Alerts
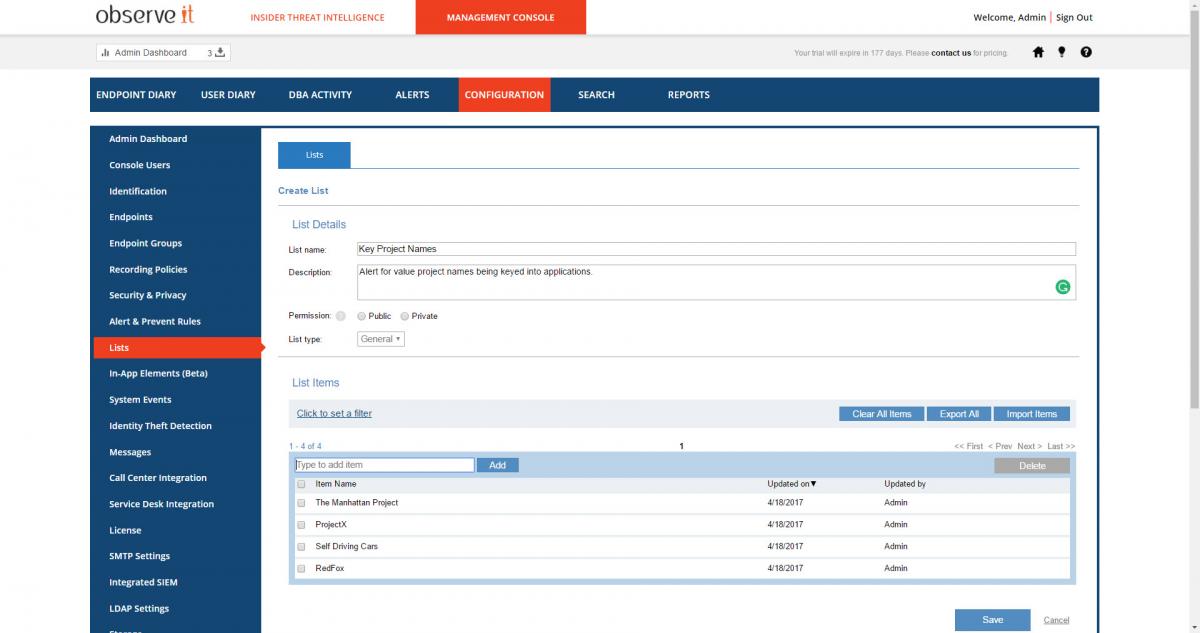
Highly requested, from Proofpoint’s 1500 client install base, came the idea of keyword alerting. This technology enables the ability to detect sensitive keywords being typed into applications and command line tools. Proofpoint can now stay even more vigilant on users with access to critical data. For example, someone keying a lucrative project name, someone google searching a high-profile client name, or someone researching how to access the dark web. This type of activity can now be easily spotted, tracked, and honed in on ensuring you have full visibility into users with the highest level of access within your organization.
Preventative Actions
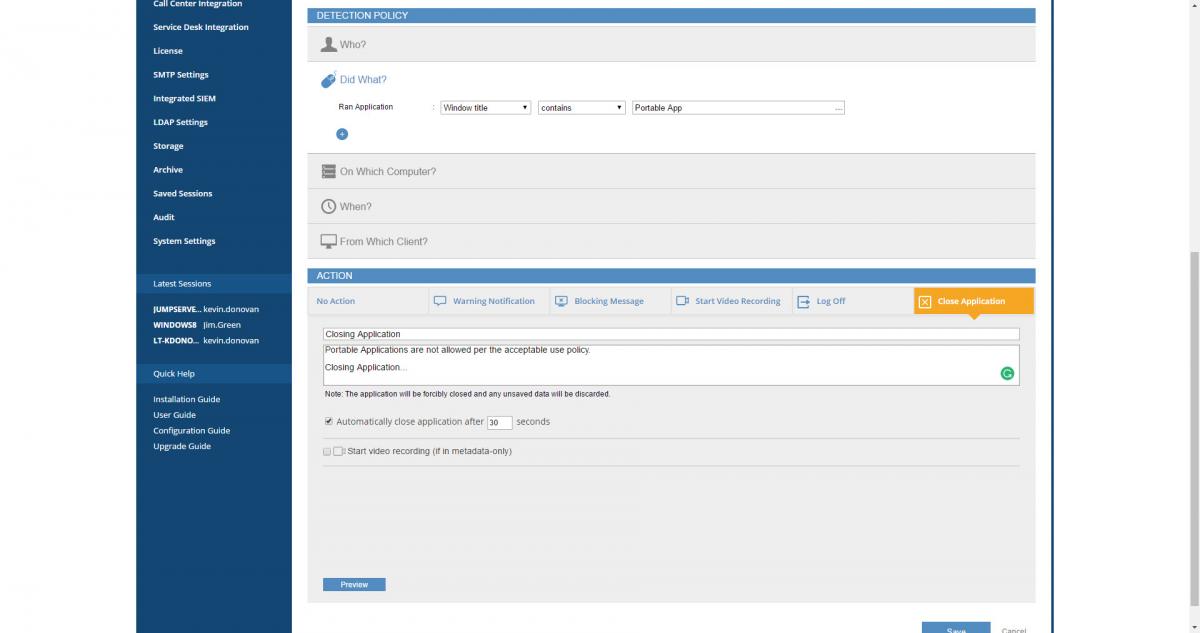
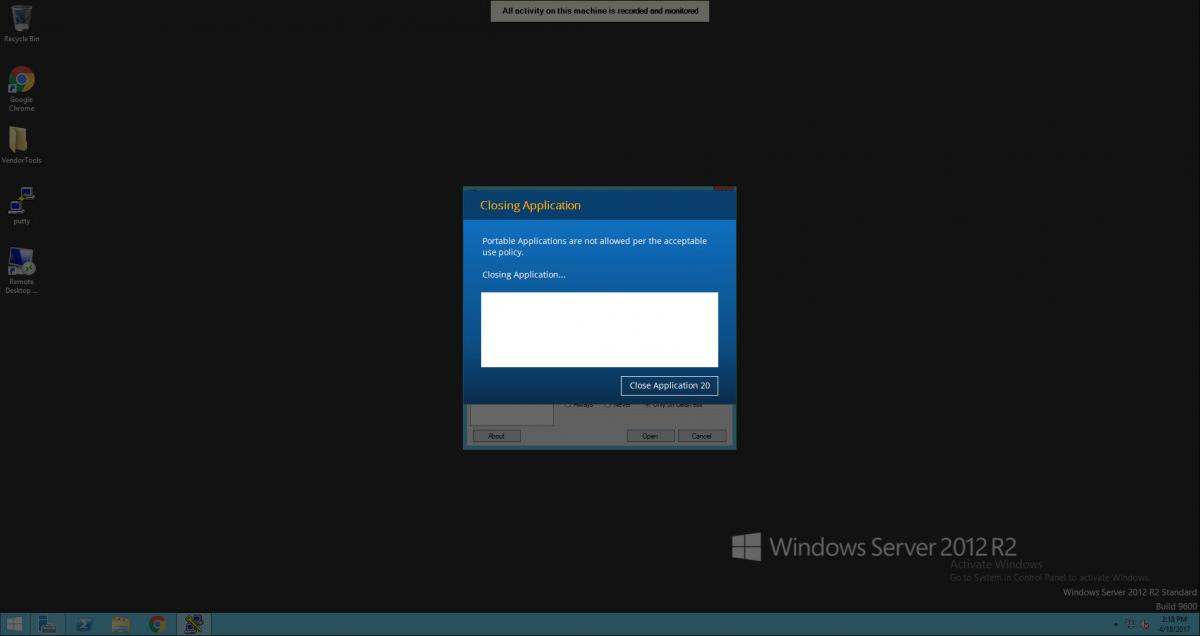
Proofpoint now offers the ability to automatically block specific user actions. Customers can leverage the Proofpoint insider threat library of more than 200 rules; when triggered, Proofpoint ITM can be configured to shut down an application or log a user out of a system. Security and IT teams can even customize their own specific rule logic to put these control sets in place. For example, they could set up a rule to block privileged users from running portable applications.
Simply follow Proofpoint ITM’s logic of who, did what, on which computer, when, and from where:
Proofpoint ITM then stands guard against out-of-policy user behavior:
Customers can take advantage of the power of user analytics and preventative controls as well as a wide range of other insider threat mitigation tools. To learn more about Proofpoint ITM 7.0, check out a quick video on the Top 4 Features of this release. If you have not already, try Proofpoint ITM out for yourself with a 15-day free trial here.
Subscribe to the Proofpoint Blog