CISO’s see servers and devices, apps and logs, traffic and clouds. With the Splunk® platform security teams are able to see data—everywhere. This kind of Operational Intelligence enables the curious to look closely at what others ignore—machine data—and find what others never see: insights that can help make a company more productive, profitable, competitive and secure. But machine data, no matter how well it’s organized, can be cumbersome to sift through when trying to swiftly investigate an Insider Attack. With Proofpoint integration, that machine data comes to life as video playback with the simple push of a button.
With Insider Threats becoming more and more prevalent in daily headline news, there is now a great need to monitor the internal business and Privileged IT user. With its pre-configured Splunk integration module, Proofpoint's user activity video logs and user activity text logs in the Splunk platform provide all the details of exactly what users are doing on the network, right from within the platform security teams trust to deliver reliable data in security oversight and compliance reporting.
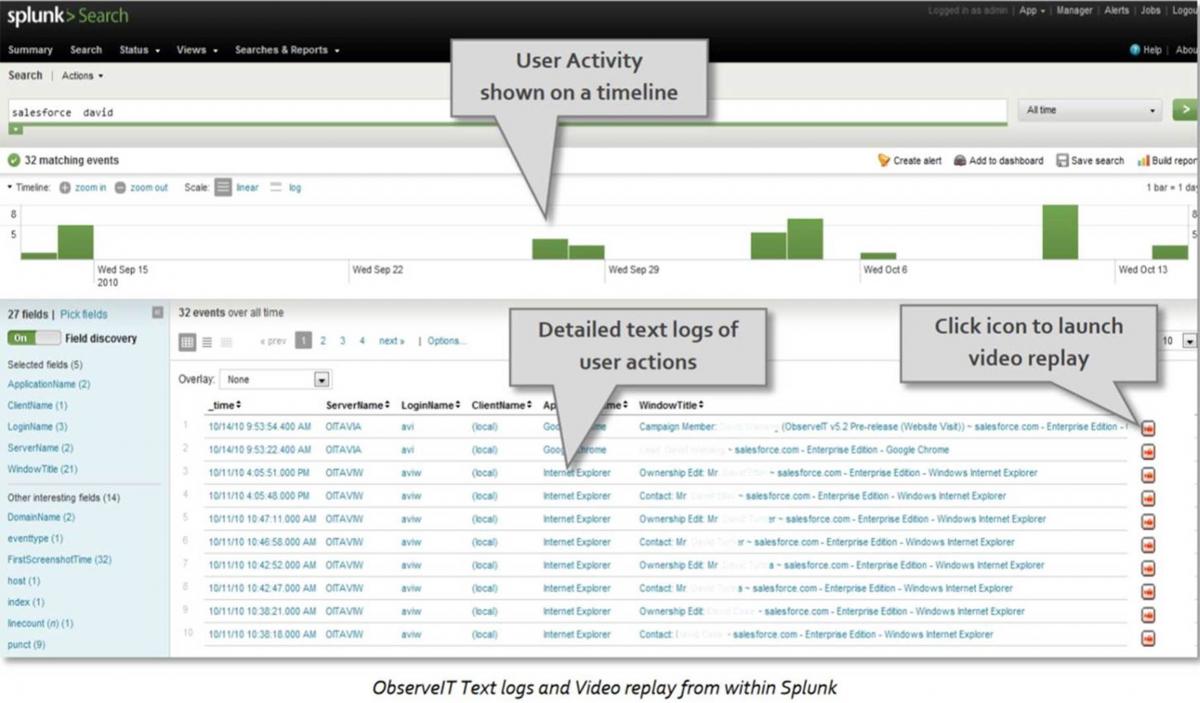
Event details are ‘dashboarded’ across a standard Splunk timeline, with event listings showing exactly what applications, URLs, files and system calls the user touched. A video replay icon is available for each specific user action, allowing investigators to launch the video replay at the exact moment in time that the user performed that action. Download a free trial version of the Proofpoint Connector for Splunk.
Imagine this scenario: The Splunk dashboard alerts the security team to a potential security incident. But now, instead of investigating by drilling down into system logs, the investigators instead just click on the "Play the Video" icon, which shows exactly what the user did!
Proofpoint takes a people-centric approach by educating the user in real time, detecting the risky user action or policy violation or data loss, and then gives the security team the ability to act on the malicious or unauthorized activity.
- With the bad actor, it does this by identifying patterns and stories of an Insider Attack
- With the negligent user, it is changing behavior of these users in real time by informing them of the company's internal security policies and then enforcing the correct behavior.
Download your 15-DAY FREE TRIAL of Proofpoint ITM now. For all the rest, including details about the app, setup instructions and more screenshots, consult the app's homepage on the Sideview website.
Existing Splunk customers interested in Proofpoint's solution, or an existing Proofpoint customer interested in Splunk, can take advantage of BOTH Splunk and Proofpoint, as they offer free versions of their product as well as Enterprise Trial versions. Whichever side you're on, bring the two worlds together by trying out the Trial version of the Proofpoint ITM connector app today.
Subscribe to the Proofpoint Blog

