Occasionally, you may need to give select users file transfer access to Linux servers to access files or upload new files.
The users may already have access to the systems using Secure Shell (SSH), for example. In some cases, the users may not already have access, or the users are not aware it is a Linux server.
These users need server access to successfully perform their jobs so granting access is not optional. But, the more access that is granted, the greater the organizational risk for data exfiltration, sabotage, and more. Expanding the scope of user access increases the likelihood the user, or someone who knows the user’s credentials, will access the server and extract data – possibly even gaining enough information to later SSH into the servers to establish admin user privileges for themselves.
What is the best method to ensure a secure but productive workplace? There are a few approaches that can be used to ensure the right users have the right ftp access level, preventing risk and data loss for the organization.
Establishing Proper Permissions:
One approach is to establish proper permissions on the file system. This approach is not easy to implement as some files that need read access can be hard to lock down completely. Maintaining it is an even greater challenge as files and directories are created, modified or removed. For example, the /etc/passwd file has read access for everyone in order to allow users into the system; however, read access can allow user to determine which users are defined as local users on the system increasing the possibility of a user stealing credentials of a local user to access additional, possibly sensitive, information. Unfortunately, there are many configuration files on the system. Locking all of them for the ftp users is very hard, sometimes even impossible, to set up and maintain.
Jailing:
Another approach is jailing or restricting user access to just one directory. While this is a better security approach than establishing proper permissions, it lacks granularity and may require changing the setup of some permissions on the system to achieve it. For example, how would you approach jailing if you want to allow a user or users to access more than one directory? What should the approach be if you have specific files you want to allow (or exclude) access - inside or outside the chroot directory? While quite strong from a security perspective, this approach may not be flexible enough for the needs of your team and organization.
Proofpoint SFTP:
Another option is to use Proofpoint to control sftp access. Using this approach, you can alert and monitor which directories the user enters and which files he accesses or gets from the ftp server. With Proofpoint 7.1, this method can prevent the user from executing file transfer actions on specific directories or file names. It can control the sftp get and put commands. More importantly, it can prevent the user from displaying directory content via sftp (dir or ls commands) or removing files he does not have the right to remove. With a centralized monitoring system, you can view actions on all systems that run the Proofpoint agent using centralized policy rather than reviewing one system at a time.
Proofpoint blocks get of /etc/passwd and view of the root file system (using the filezilla client)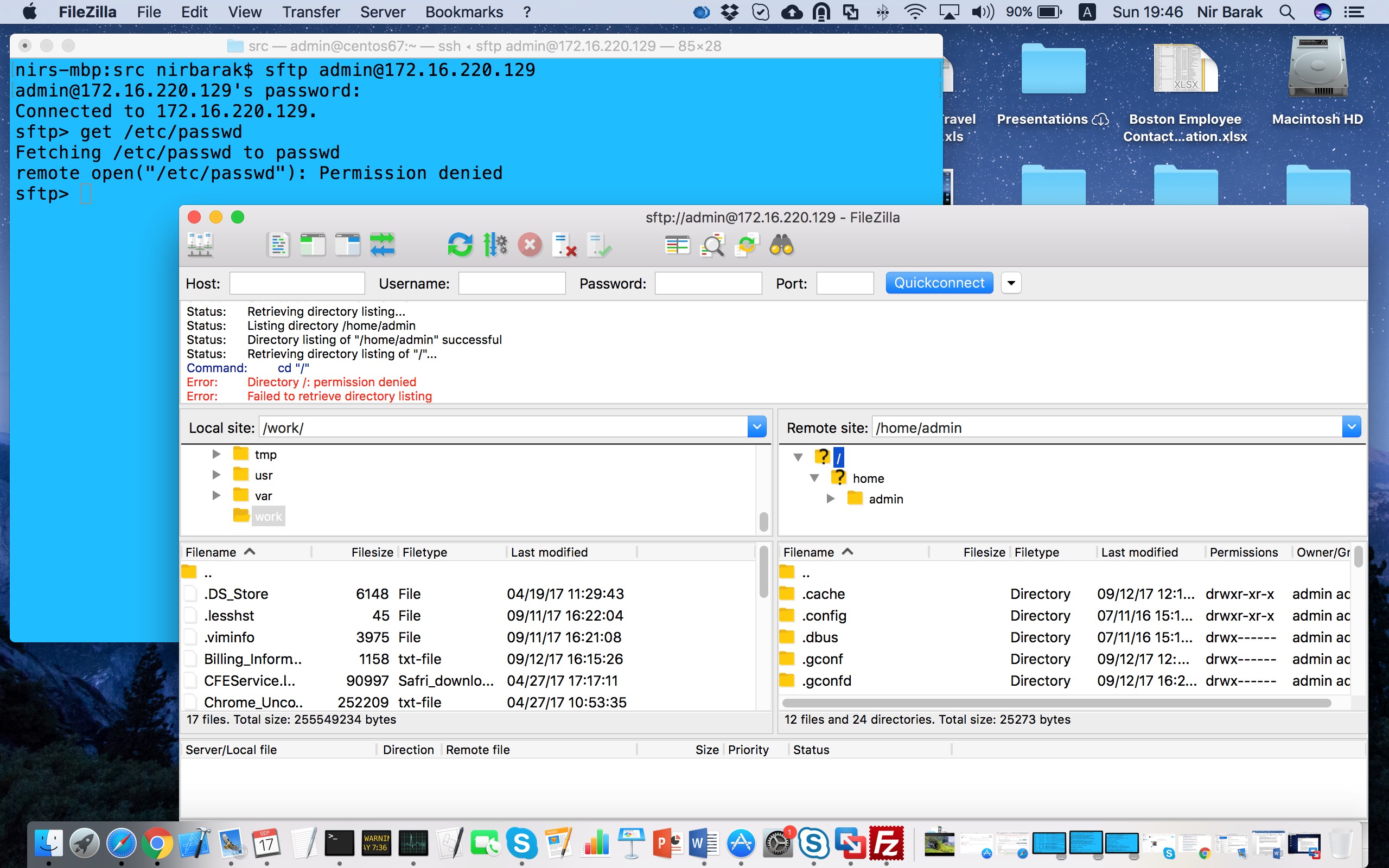
This approach may be the flexible, yet secure, solution you need to ensure sftp access control - especially given the tool works the same regardless of the sftp client that is working against the Linux server.
Give it a try - download the free trial.
Subscribe to the Proofpoint Blog

