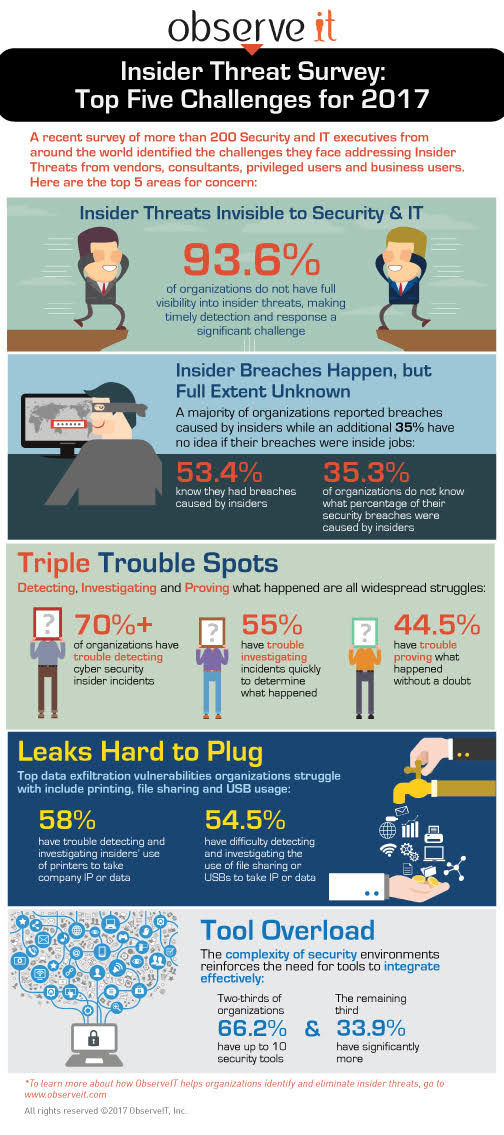
According to the latest Verizon DBIR report, 90% of all security issues stem from insiders, whether intent is malicious or accidental. With increasing attention being placed on the risks associated with vendors, contractors, privileged users, high-risk employees and everyday business users, there is no doubt organizations must combat insider threats. But where do you start when perceived challenges include: How many tools are too many? What’s the best way to plug and prevent data exfiltration leaks? What is the best way to deter malicious or negligent actions putting the company at risk? How does an organization detect, investigate and prove what happened once an incident occurs?
A recent survey of more than 200 Security and IT executives from around the world highlighted the challenges they face addressing Insider Threats.
5 Insider Threat Challenges in 2017
Final Thoughts
Based on these statistics, having a single, comprehensive insider threat management solution installed is more important than ever. This solution must include features such as insider threat detection, incident investigation, and real-time alerts.
Learn more about Proofpoint's insider threat management solution and see how it solves all these challenges with industry-leading monitoring and analytics tools.
Subscribe to the Proofpoint Blog

