Recently, the NSA discovered that one of their cybersecurity specialists, Harold Martin III, had been stealing top-secret data—to the tune of 50 terabytes—over the course of two decades using removable media devices. He managed to steal even more data than Edward Snowden leaked a few years back—impressive for Martin and, to put it mildly, bad news for the NSA.
As this insider threat story illustrates, even in the age of cheap and ubiquitous cloud storage, old-school removable media like USB devices are still popular for both legitimate business uses and illegitimate data exfiltration purposes. Insiders like Harold Martin often rely on removable media like flash drives and keyboard shortcuts like copy/paste and print screen to exfiltrate data from sensitive locations—whether their motives are benign or criminal. These activities usually happen on the endpoint and don’t touch the network, which means they are difficult to monitor and thwart.
Recent security events like this have spotlighted an urgent need to define a new approach to insider threat management in a post-DLP world by addressing gaps in visibility and context.
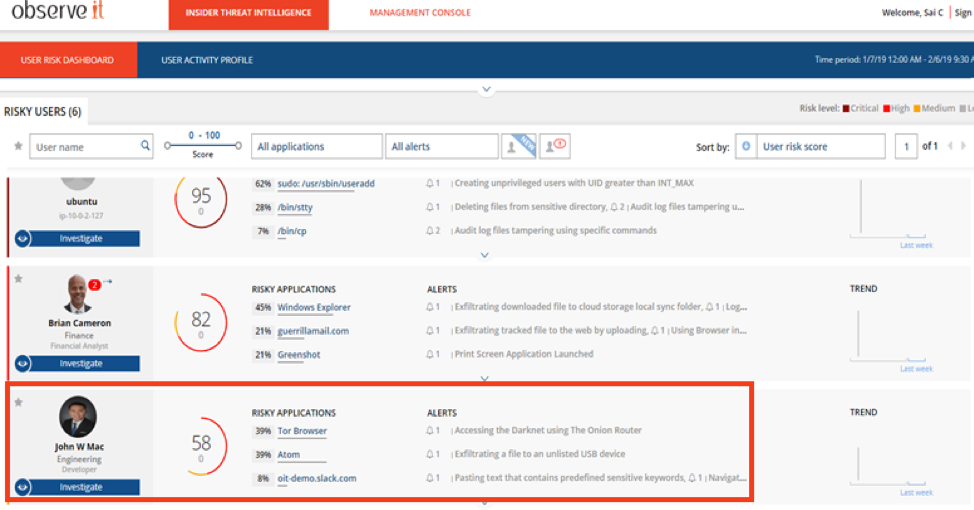 The Risk Dashboard above highlights an example of alerts that could appear when a user attempts to exfiltrate data through an unapproved removable media device.
The Risk Dashboard above highlights an example of alerts that could appear when a user attempts to exfiltrate data through an unapproved removable media device.
Because it’s unrealistic to completely block removable media at most organizations, data exfiltration attempts using these devices can be challenging to prevent outright. Keyboard shortcuts and print jobs are similarly impossible to take out of the equation.
Since our customers continually face insiders making use of these threat vectors, our team has been busy behind the scenes building new capabilities into Proofpoint.
Today, we’re launching Proofpoint 7.7, which includes insider threat management capabilities to provide a modern approach to data loss prevention (DLP). It delivers increased data exfiltration capabilities and further protects against insider threats, specifically reducing the risk of data loss while enabling streamlined investigations.
Our customers will now have a brand-new arsenal of tools at their disposal to reduce the risk of data exfiltration through endpoint channels (including via removable media and keyboard shortcuts) and to streamline investigations into these incidents.
Reduce the Risk of Data Exfiltration Through Endpoints
Proofpoint's insider threat software now detects users exfiltrating data through removable media and using keyboard shortcuts such as:
- Copy/paste
- Cut/paste
- Print screen
- Various application-specific special keystrokes
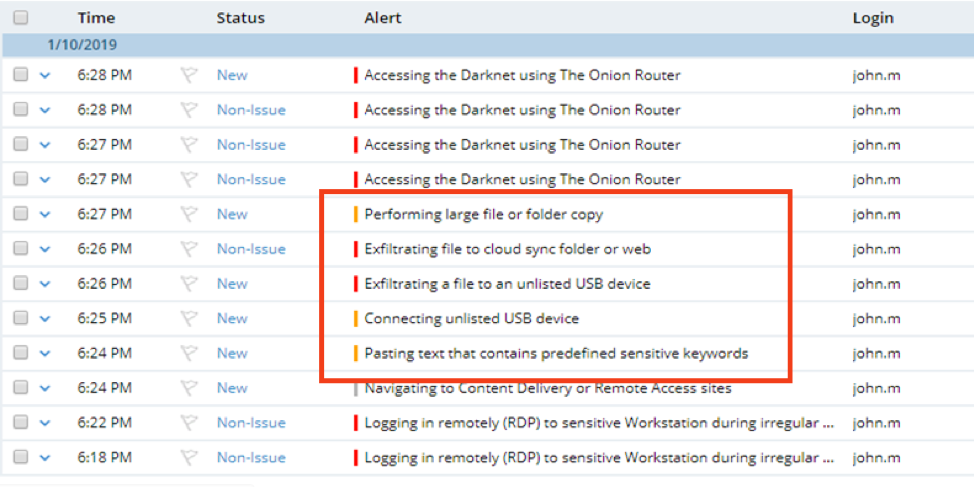 The screenshot above demonstrates what happens when a user receives multiple alerts due to suspicious activity. The user will have seen the alerts on his screen, and the IT or security admin will be able to view them on the dashboard above.
The screenshot above demonstrates what happens when a user receives multiple alerts due to suspicious activity. The user will have seen the alerts on his screen, and the IT or security admin will be able to view them on the dashboard above.
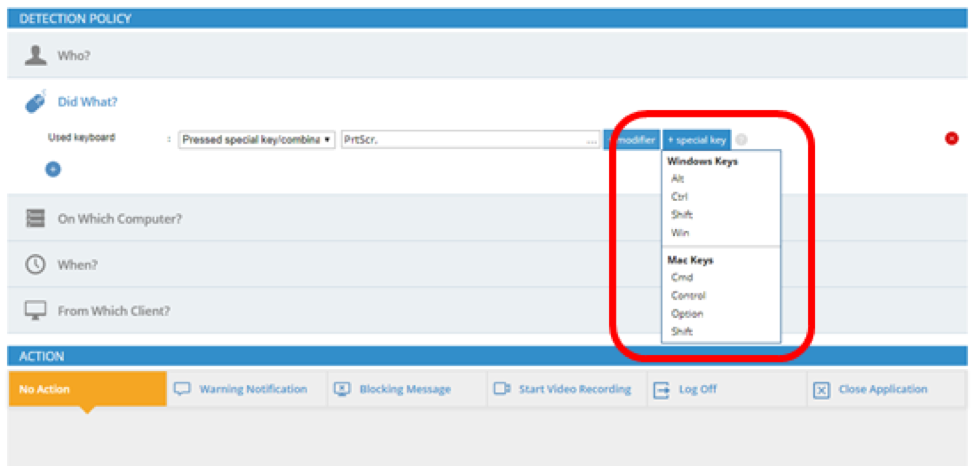 The screenshot above illustrates the various keyboard shortcuts and hotkeys that may be indicators of data exfiltration (across both PC and Mac use cases).
The screenshot above illustrates the various keyboard shortcuts and hotkeys that may be indicators of data exfiltration (across both PC and Mac use cases).
These new capabilities will bolster Proofpoint's library of 350+ insider threat indicators, built with the guidance of CERT’s Insider Threat Center. The ultimate goal is to help organizations decrease the risk of data exfiltration—in particular via user endpoints.
Let’s take a look at how these capabilities can be used.
Escalate Risk Level
First of all, organizations will now be able to escalate the risk level of users attempting to exfiltrate files using keyboard shortcuts or removable media. This will enable organizations to carefully monitor users who have displayed risky behavior related to these vectors in the past. While not every user who plugs in a USB device is stealing company secrets, this can be a valuable piece of context as part of a larger investigation.
Risk-Based Prioritization
As security pros know all too well, it can be tough to sort the signal from the noise when it comes to alerts, which can lead to plenty of alert fatigue for teams. Proofpoint 7.7 can help. Now, whether conducting proactive insider threat hunting or reactive investigations, security analysts have access to a prioritized view of user activities, indicating when suspicious removable media, keyboard shortcuts, or print jobs were used on specific endpoints. This way analysts know exactly where to start and can scrutinize the riskiest behaviors first.
Mitigate Insider Threats
Our customers will also be able to choose various insider threat mitigation strategies related to these data exfiltration vectors such as:
- Logging the user out of a questionable session
- Educating the user in real-time via alerts about policy violations
- Providing the security team with visibility as the threat progresses
Organizations can decide for themselves which of these mitigation strategies make the most sense in a given instance, or apply a certain tactic across the board, depending on their unique security needs and preferences.
Investigate Faster and More Accurately
Finally, and perhaps most importantly, Proofpoint 7.7 features improvements to our easily searchable dashboard, offering more insight into risky user actions and data movement. This will enable investigators to get answers even more quickly and with a high degree of accuracy.
Frequently, data exfiltration through endpoint channels involves files being moved from sensitive locations, modified to avoid existing monitoring tools, and finally exfiltrated out of the organization through removable media.
With Proofpoint 7.7, security analysts have access to even more context around the who, what, where, when and why of file, device and user history in one security event timeline—both within our console and through our APIs. This means they can quickly spot instances of the type of data exfiltration described above and take action to mitigate risk.
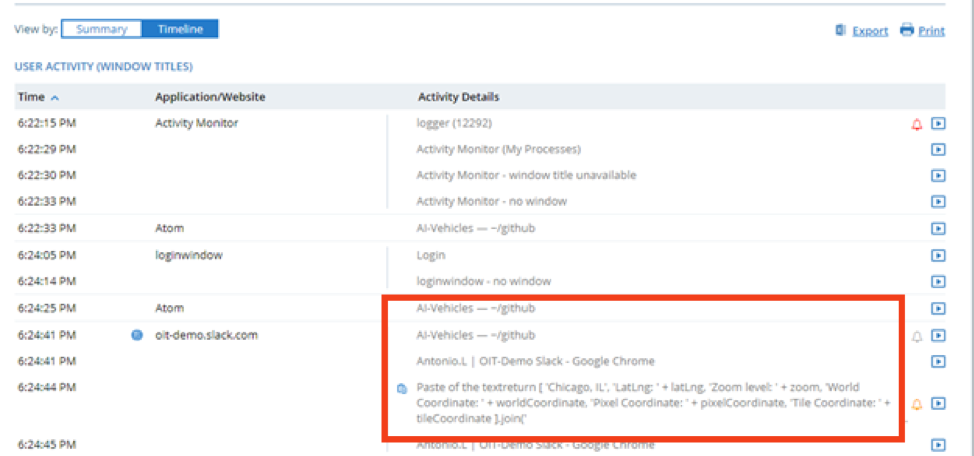 The image above shows the level of context Proofpoint ITM provides around a copy/paste-related insider threat alert. In this case, the user clearly checked into Github, looked at the AI-vehicles folder/file, and then copy/pasted a chunk of text (potentially proprietary information) into a Slack conversation. In other words, sensitive information was transferred to a potentially unapproved app.
The image above shows the level of context Proofpoint ITM provides around a copy/paste-related insider threat alert. In this case, the user clearly checked into Github, looked at the AI-vehicles folder/file, and then copy/pasted a chunk of text (potentially proprietary information) into a Slack conversation. In other words, sensitive information was transferred to a potentially unapproved app.
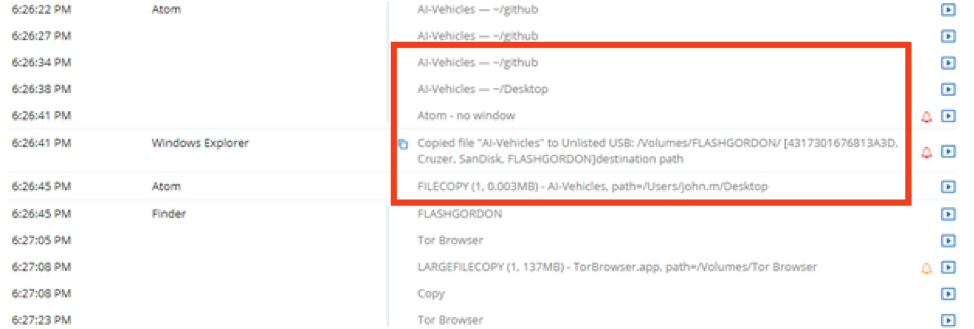 Above, it becomes clear that the same user then copied more sensitive files related to proprietary IP to an unlisted USB Drive and then visited a Tor browser (which is private and anonymous, and often associated with Dark Web activities). These are both very risky user actions, and likely indicators of an insider threat in progress.
Above, it becomes clear that the same user then copied more sensitive files related to proprietary IP to an unlisted USB Drive and then visited a Tor browser (which is private and anonymous, and often associated with Dark Web activities). These are both very risky user actions, and likely indicators of an insider threat in progress.
Increasing Visibility to Decrease Insider Threat Risk
Traditional data exfiltration solutions (including data loss prevention solutions) provide little visibility into risky user interactions (like copy/pasting, taking screenshots and USB drive usage) with sensitive data on the endpoint, and they are often time-consuming to set up and maintain. Even mature security teams using data loss prevention technologies generally require deeper user visibility to balance efficient business operations and effective security.
Enter Proofpoint 7.7: Our new data exfiltration prevention capabilities make it possible to effectively decrease insider threat risk via endpoint-related vectors, while maintaining the ease of use and lightweight agents that Proofpoint customers value most.
Ready to give Proofpoint 7.7 a shot?
Existing customers:
New to Proofpoint?
